A Guide to Software Project Risk Management
Master software project risk management with our guide. Learn to identify, analyze, and mitigate technical risks to ensure project success and ROI.

Let's be honest, software project risk management isn't about filling out forms or creating endless paperwork. It’s a strategic game of navigating uncertainty to make sure your project actually delivers a return on investment.
At its core, it's the systematic process of identifying, analyzing, and responding to potential threats before they have a chance to blow up your project. This is the real difference between just crossing your fingers and hoping for the best versus actively engineering for a successful outcome.
The Strategic Value of Risk Management
Imagine you're building a skyscraper in downtown San Francisco. You wouldn't just start digging without architects and structural engineers who have a rock-solid plan for handling earthquakes. These experts don't sit around waiting for the ground to shake—they anticipate it. They meticulously calculate load tolerances, model every conceivable stress point, and build in redundancies to keep the structure standing.
That's exactly what effective software project risk management is for your project. It's your engineering plan for the digital world, giving you a technical, actionable framework that moves you beyond pure guesswork. Instead of frantically reacting to disasters, you can systematically get ahead of threats like scope creep, technical debt, and budget overruns before they crack your project's foundation.
Protecting Your Project Investment
Taking a proactive stance on risk pays off in tangible ways that go far beyond just dodging problems. Think of it as an investment in efficiency, predictability, and, ultimately, your project's success.
When you bake risk management into your process, you empower your team to:
- Safeguard the Budget and Timeline: Spot potential financial or scheduling risks early using CI/CD pipeline checks and financial forecasting models.
- Improve Decision-Making: Leverage quantitative data—like Expected Monetary Value (EMV) calculations and Monte Carlo simulations—to choose technologies based on risk exposure, not buzz.
- Increase Stakeholder Confidence: Publish a real-time risk dashboard (e.g., Grafana + Prometheus) to prove you're on top of threats and earning trust with transparent metrics.
A formal risk management process completely shifts your team's mindset from reactive firefighting to proactive problem-solving. It builds a culture of foresight, where everyone is empowered to flag potential hurdles before they become full-blown crises, ensuring the project stays resilient and on track to hit its goals.
The Proactive Risk Management Framework
Effective risk management in a software project isn't a one-off meeting you can check off a list. It's a disciplined, continuous cycle. The goal is to shift from scrambling to put out fires (reactive) to having a clear, repeatable process for handling uncertainty before it blows up your project (proactive).
This whole process breaks down into four essential phases. Each one builds on the last, creating a logical flow that turns abstract worries into a concrete, actionable plan. This is how you systematically de-risk a project and stay in control.

Phase 1: Risk Identification
First things first, you have to find potential threats before they find you. This isn't about gazing into a crystal ball; it's a systematic discovery process. The idea is to create a master list of anything and everything that could derail your project's budget, timeline, or quality.
Key techniques:
- Automated Code Analysis: Integrate tools like SonarQube, OWASP Dependency-Check, and Snyk in your CI pipeline to detect security vulnerabilities and outdated libraries.
- Brainstorming Sessions: Get devs, architects, security engineers, and stakeholders in a virtual room (or use Miro) to map out risks by system component.
- Service Logs & Metrics Review: Analyze historical metrics (CPU, memory, error rates) via Prometheus/Grafana to identify recurring performance or availability issues.
- Documentation Reviews: Examine past post-mortems, architecture decision records (ADRs), and incident reports to surface gremlins that have bitten you before.
Phase 2: Risk Analysis
Okay, you have your list. Now what? The next step is to analyze and prioritize. Not all risks are created equal—some are minor bumps in the road, while others are full-blown project killers. This is where you figure out which ones deserve your immediate attention.
Activities:
- Qualitative Analysis: Rate each risk on a 1–5 scale for Probability and Impact, then plot them on a heatmap. Use tools like Excel or a JavaScript library (e.g., D3.js) to generate real-time charts.
- Quantitative Analysis: For high-priority risks, calculate the Expected Monetary Value (EMV):
EMV = Probability (%) × Potential Cost ($)Example:
Probability = 0.40, Cost = $50,000 → EMV = 0.40 × 50,000 = $20,000 - Monte Carlo Simulation: Run thousands of project schedule scenarios (using Python packages like
uncertaintiesor specialized modules in your RMIS) to forecast realistic completion dates and confidence intervals.
Phase 3: Risk Response Planning
With your risks analyzed and stacked by priority, it's time to decide what you're actually going to do about them. This is where you build your action plan. For any significant threat, you generally have four strategic options.
Your main strategies are:
- Avoid: Eliminate the risk at the source. For example, replace an experimental microservice framework with a proven one (e.g., switching to Node.js Express + REST standards).
- Mitigate: Implement specific countermeasures, such as adding circuit breakers (Hystrix) or canary releases to limit blast radius.
- Transfer: Offload risk via SLAs or insurance. Craft contractual clauses per best practices in mastering the contract risk management process.
- Accept: Acknowledge low-impact risks and build budget buffers for them. Document acceptance criteria and contingency triggers in your risk register.
Phase 4: Risk Monitoring and Control
This final phase isn't really a "final" phase at all—it’s an ongoing process that lasts for the entire project. It’s all about tracking your identified risks, keeping an eye out for new ones, and checking if your response plans are actually working.
Tactics:
- Real-Time Dashboards: Use Grafana to visualize risk score trends and alert on threshold breaches (e.g., total EMV > $100K).
- Automated Alerts: Configure Slack or email notifications when a risk’s status changes or a metric drifts into the danger zone.
- Risk Audits: Schedule bi-weekly risk health checks—review the Risk Register, validate residual risk levels, and retire closed items.
Organizations with mature project management practices hit their goals 77% of the time versus 63% for less mature teams. Investing in a solid framework is a direct investment in your project's success. If you're curious about maturity models, read more here: https://opsmoon.com/blog/devops-maturity-levels.
How to Identify and Analyze Technical Risks
Alright, let's move from theory to the trenches. Having a vague idea of what might go wrong isn't enough. You need to get your hands dirty with structured, repeatable methods for digging up and evaluating the real threats lurking in your project. It’s about being a detective, not just a worrier.
Start with a Map: The Risk Breakdown Structure
A Risk Breakdown Structure (RBS) organizes your search by category, ensuring comprehensive coverage. Example (YAML format):
RBS:
Technical:
- Architecture & Design:
- Scalability wall
- Legacy integration complexity
- Unstable API contracts
- Technology Stack:
- Niche framework skill gap
- Unpatched dependencies
- Security:
- Injection vulnerabilities
- Weak encryption
Organizational:
- Resources:
- Key dev departure
- Budget cuts in cloud services
- Communication:
- Misaligned stakeholder requirements
External:
- Vendor Dependencies:
- Third-party service bankruptcy
- Market Changes:
- Competitor feature launch
Dig Deeper: Getting to the Root of the Problem
Root Cause Analysis (RCA) separates symptoms from true issues:
- Ishikawa (Fishbone) Diagrams: Visualize cause categories (People, Process, Technology, Environment).
- The 5 Whys: Iteratively ask "Why?" until you uncover the fundamental flaw.
Blend this with strategies for identifying and analyzing technical debt, such as static code metrics (cyclomatic complexity, code churn) to quantify hidden liabilities.
Common Software Project Risks and Initial Analysis
| Risk Category | Specific Risk Example | Potential Impact | Typical Probability | Early Warning Signs |
|---|---|---|---|---|
| Technical | Unforeseen Integration Complexity | Delays, scope creep, budget overruns | Medium to High | Vague API docs, no sandbox environments, mismatched data models |
| Technical | Performance Bottlenecks | Poor UX, system crashes, inability to scale | Medium | High CPU/memory usage, slow CI performance, complex DB queries |
| Organizational | Scope Creep | Missed deadlines, burnout, budget exhaustion | High | Frequent change requests, feature bloat, unclear acceptance criteria |
| Organizational | Key Personnel Loss | Knowledge gaps, project slowdown, low morale | Low to Medium | Single point of failure, declining team engagement |
| External | Third-Party Vendor Failure | Outages, data loss, emergency replacement dev | Low | Vendor financial instability, poor support SLAs |
From "Maybe" to "How Bad?": Using a Risk Matrix
A Probability & Impact Matrix assigns numerical values (1–5) and computes a Risk Score (Probability × Impact). For example:
- Probability = 4, Impact = 5 → Score = 20 → Red zone
- Probability = 2, Impact = 1 → Score = 2 → Low priority
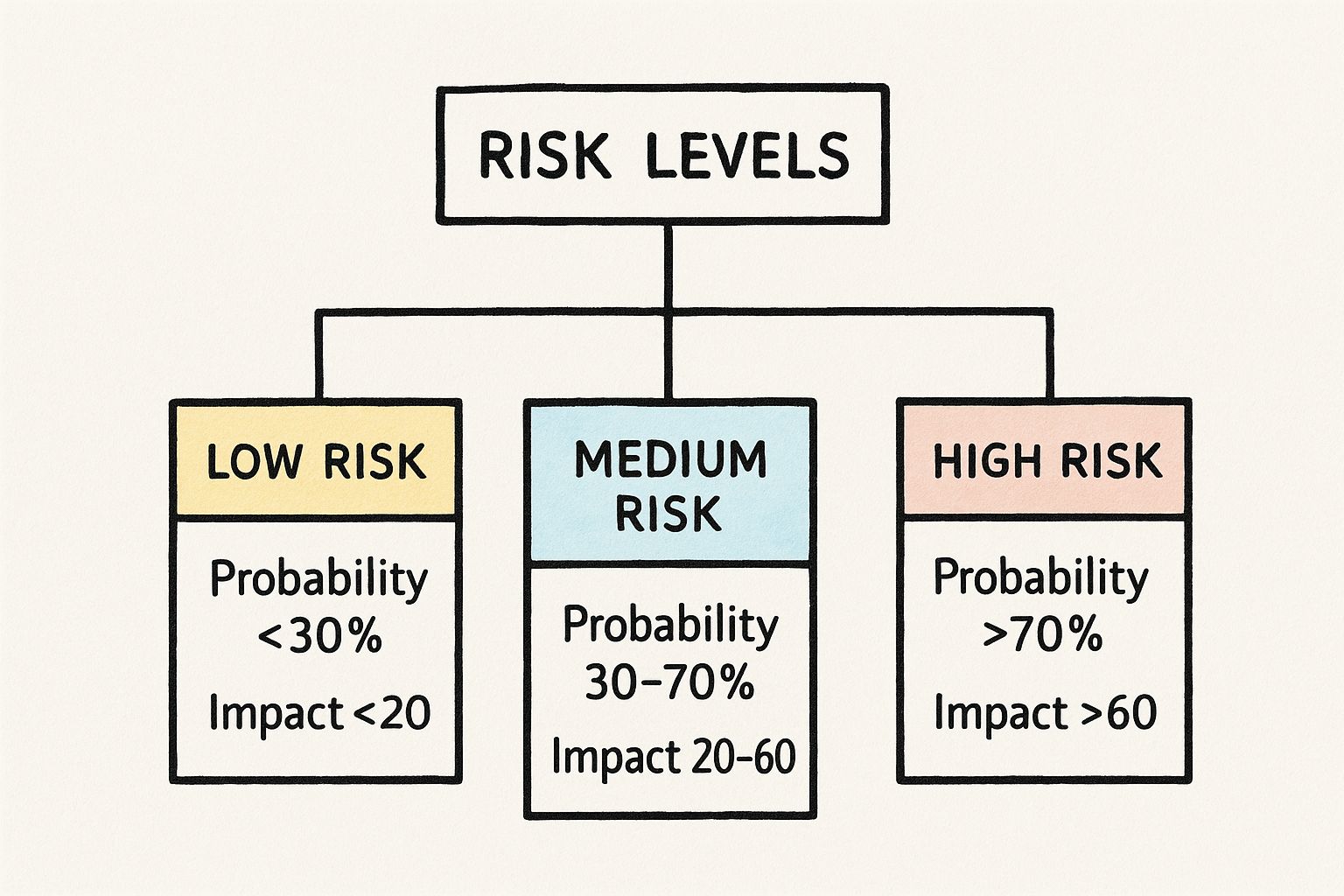
This flows directly into your DevOps pipeline, tying risk levels to deployment gates and quality checks. To see how this fits, check our guide on the 5 phases of the software development life cycle.
Building Your Risk Mitigation Strategy
You've mapped out the minefield and pinpointed the biggest threats. Now it's time for action. This is your risk response playbook—granular instructions for when a threat pops up.

The Four Core Risk Response Strategies
- Avoid: Change scope/tech. E.g., choose React or Angular instead of an unstable experimental framework.
- Transfer: Offload via SaaS/SLAs. E.g., use Amazon RDS or Azure SQL Database to transfer backup and patch responsibilities.
- Mitigate: Reduce probability/impact. E.g., implement caching layers (Redis), optimize database indices, add load-test suites (JMeter, k6).
- Accept: For negligible risks, document acceptance and budget a small contingency fund.
Research shows nearly 10% of every project dollar is wasted on poor risk management. Over 85% of PMs juggle multiple projects, making it easy to overlook threats. Dive into project management statistics for more context.
Centralizing Your Strategy: The Risk Register
Your Risk Register is the single source of truth. A technical, actionable schema:
| Field | Description |
|---|---|
| Risk ID | Unique code (e.g., TECH-001) |
| Risk Description | Concise problem summary |
| Category | Technical, Organizational, External |
| Probability & Impact | Numeric ratings (1–5) |
| Risk Score | Probability × Impact |
| Response Strategy | Avoid, Transfer, Mitigate, Accept |
| Mitigation Plan | Step-by-step actions (e.g., “Implement Redis cache on payment API by Sprint 5”) |
| Risk Owner | Single accountable individual (role and name) |
| Status | Open, In Progress, Closed |
You can automate entries via a simple Jira API script:
curl -X POST -H "Content-Type: application/json" -u user:token \
'https://your-jira-instance/rest/api/2/issue' \
-d '{
"fields": {
"project": {"key": "PROJ"},
"summary": "TECH-001: Unforeseen Integration Complexity",
"issuetype": {"name": "Risk"},
"customfield_10000": 4, // Probability
"customfield_10001": 5, // Impact
"description": "API docs incomplete; vendor sandbox unavailable."
}
}'
By meticulously documenting each risk and its response plan in one central place, you turn abstract worries into a concrete playbook. This creates accountability and gives your team the clarity they need to navigate the inevitable project storms.
Embedding Risk Management in Agile Workflows
Trying to manage risk with a big, upfront plan that you never touch again just doesn't fly in Agile. The old waterfall approach is broken for modern development. You need to weave risk management directly into your Agile ceremonies.
Integrating Risk into Agile Ceremonies
Leverage existing meetings:
- Sprint Planning: Add a “risk check” question per user story: “What dependencies or unknowns could block this?”
- Backlog Grooming: Tag uncertain stories with a “Spike” issue type and allocate 1–2 days to research.
By making risk a standard part of sprint planning and grooming, you shift the team's focus from what to build to how to build it successfully.
Using Retrospectives for Continuous Improvement
In retrospectives, ask:
- “Which risks caught us off guard this sprint?”
- “How effective were our mitigation steps?”
- “What process tweak can prevent recurrence?”
This feedback loop sharpens your risk controls every sprint.
Visualizing Progress with a Risk Burndown Chart
A Risk Burndown Chart tracks total risk exposure over time:
- Quantify: Sum all active risk scores (Probability × Impact).
- Chart: Plot total exposure at the end of each sprint.
- Monitor: Watch the trend—declining slope indicates effective mitigation.
This chart provides transparency and motivates the team by visualizing risk reduction.
Using Software to Automate Risk Management
Managing modern project risks with a static spreadsheet is like navigating with a paper map. You need dynamic, data-driven tools.
Tools like Jira (with Risk Register plugins) and Asana become your RMIS:
- Link Risks to Work Items: Associate risks directly with epics, stories, or tasks for traceability.
- Real-Time Dashboards: Visualize risk exposure trends and overdue countermeasures.
- Advanced Simulation: Use built-in Monte Carlo features to forecast schedule and cost uncertainty.
- Automated Reminders: Configure email/Slack alerts for pending mitigation tasks or status changes.
The global project management software market is valued at $7.24 billion, projected to exceed $12 billion by 2030. Yet 23% of organizations still use manual methods, leaving huge gains on the table.
This level of integration is a cornerstone of effective DevOps. By automating processes, you free engineers to focus on building great software. For more, see the benefits of workflow automation.
Software Risk Management FAQs

What is the biggest mistake in software project risk management?
Treating risk management as a one-time setup at project start. A register that gathers dust is worse than useless.
Tactics to avoid this:
- Enforce risk reviews in each sprint ceremony.
- Embed daily standup checks: “Anything new we should flag?”
- Automate reminders in your PM tool for overdue risk entries.
How do you get stakeholder buy-in for a formal risk process?
Speak their language: time and money. Present the cost of inaction with data, propose a small pilot on one critical feature, and share outcomes to demonstrate ROI.
What makes a good risk owner and why is it essential?
A risk owner is accountable for monitoring and executing the response plan. They must have authority to trigger mitigation actions and communicate status. Without dedicated owners, risks slip through the cracks.
What is the difference between a risk and an issue?
| Aspect | Risk (Potential) | Issue (Materialized) |
|---|---|---|
| Occurrence | May happen in the future | Happening now |
| Impact Timing | Future uncertainty | Immediate problem |
| Example | Third-party API pricing might spike | API provider just increased costs by 300% |
Understanding this distinction helps teams stay proactive instead of reactive.
OpsMoon helps you implement robust software project risk management with expert DevOps support. Start a free work planning session to see how we can help.
