7 Infrastructure as Code Examples to Master DevOps in 2025
Explore 7 technical infrastructure as code examples using Terraform, Pulumi & more. Deep dive into code, strategy, and actionable tips to level up your DevOps.
Moving from manual configuration to automated infrastructure management is a critical step for any team aiming for scalability, consistency, and speed. Infrastructure as Code (IaC) transforms this process by allowing you to define, deploy, and manage your infrastructure using version-controlled, human-readable code. This approach eliminates configuration drift, accelerates deployment cycles, and makes infrastructure a repeatable, testable component of your software development lifecycle.
This article cuts straight to the practical application, providing a detailed look at real-world infrastructure as code examples. We will deconstruct specific use cases across a range of powerful tools, including Terraform, AWS CloudFormation, Ansible, and Pulumi. Before diving into these specific examples, understanding how IaC fits into the bigger picture of IT automation is helpful. For a broader overview of the ecosystem, you can explore this guide on various infrastructure automation tools.
Instead of just showing you code, we will analyze the strategic thinking behind each example. You will gain actionable insights and replicable methods for:
- Provisioning cloud resources in a modular, reusable way.
- Automating complex, multi-service application deployments.
- Managing configuration for servers and applications consistently.
- Implementing best practices for security, state management, and collaboration.
Each section provides the code, the context, and the tactical takeaways you need to apply these patterns to your own projects immediately.
1. Terraform by HashiCorp
Terraform is a powerful open-source tool that has become a cornerstone of modern infrastructure as code (IaC) practices. Created by HashiCorp, it uses a declarative language called HashiCorp Configuration Language (HCL) to let you define and provision data center infrastructure. Instead of manually clicking through a cloud provider's console, you write code that specifies your desired state, and Terraform handles the rest, figuring out how to achieve that state efficiently and safely.
One of Terraform's most significant advantages is its provider-agnostic nature. It can manage infrastructure across a vast ecosystem of cloud providers like AWS, Azure, and Google Cloud, as well as on-premises solutions. This makes it an ideal choice for multi-cloud or hybrid-cloud strategies, a common requirement for scaling companies. For example, Shopify uses Terraform to manage its complex Kubernetes clusters, while Netflix leverages it to orchestrate its global, multi-cloud infrastructure, showcasing its power in enterprise-level infrastructure as code examples.
This infographic summarizes the core features that make Terraform a dominant force in the IaC landscape.
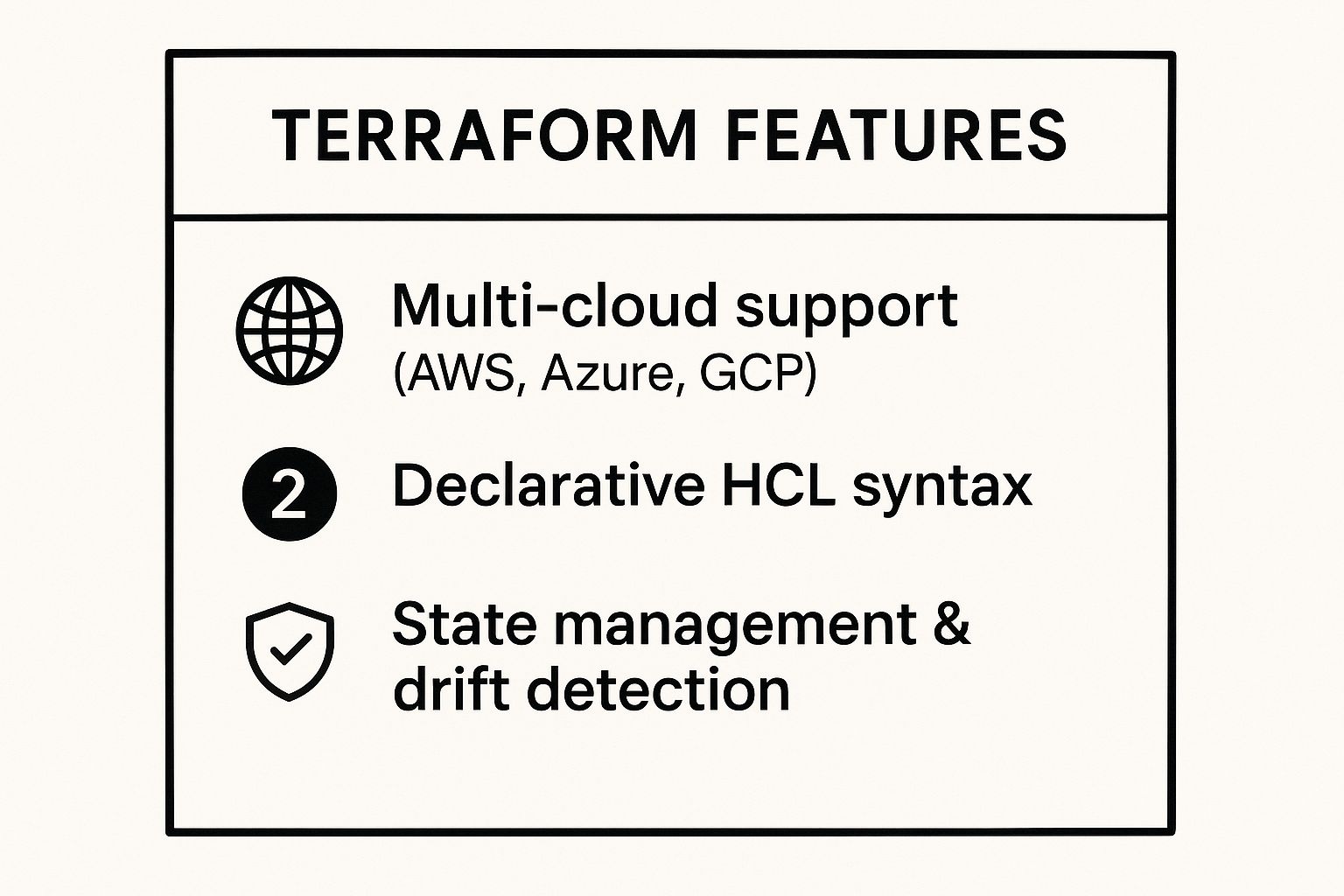
The combination of multi-cloud support, a clear declarative syntax, and robust state management allows teams to build reproducible and predictable infrastructure.
Why and When to Use Terraform
Terraform excels when you need to manage complex, multi-component environments or operate across different cloud providers. Its state file acts as a source of truth, tracking your resources and their dependencies. This allows for powerful commands like terraform plan, which provides an execution preview before any changes are made, preventing costly mistakes.
Actionable Tips for Implementation
- Remote State and Locking: Always use a remote backend like Amazon S3 or Terraform Cloud. This centralizes the state file and enables state locking, which is critical for preventing concurrent runs from corrupting your infrastructure.
- Implementation Code:
# main.tf terraform { backend "s3" { bucket = "my-terraform-state-bucket" key = "global/s3/terraform.tfstate" region = "us-east-1" dynamodb_table = "terraform-locks" encrypt = true } }
- Implementation Code:
- Modularize Everything: Break down your infrastructure into reusable modules. A module for a VPC, another for a database, and another for an application server can be composed together, drastically reducing code duplication and improving maintainability.
- Example Module Structure:
/vpc ├── main.tf ├── variables.tf └── outputs.tf /main_project ├── main.tf (calls the vpc module)
- Example Module Structure:
- Secrets Management: Never hardcode secrets in your configuration files. Use a dedicated secrets management tool like HashiCorp Vault or a cloud provider's native service (e.g., AWS Secrets Manager) and reference secrets dynamically.
- Implementation Code (AWS Secrets Manager):
data "aws_secretsmanager_secret_version" "db_credentials" { secret_id = "arn:aws:secretsmanager:us-east-1:123456789012:secret:db-creds-AbCdEf" } resource "aws_db_instance" "default" { # ... other configurations username = jsondecode(data.aws_secretsmanager_secret_version.db_credentials.secret_string)["username"] password = jsondecode(data.aws_secretsmanager_secret_version.db_credentials.secret_string)["password"] }
- Implementation Code (AWS Secrets Manager):
2. AWS CloudFormation
AWS CloudFormation is Amazon's native infrastructure as code service, deeply integrated into the AWS ecosystem. It allows you to model, provision, and manage a collection of related AWS and third-party resources by treating infrastructure as code. Using simple text files in either YAML or JSON format, you define your desired resources and their dependencies, and CloudFormation provisions and configures them for you in a predictable and orderly manner.
As a service native to AWS, CloudFormation offers unparalleled integration with AWS services, making it a go-to choice for teams operating exclusively within the Amazon cloud. This tight coupling ensures that new AWS features and services are often supported in CloudFormation from day one. For instance, financial giant Capital One leverages CloudFormation to enforce strict compliance and security policies across its cloud infrastructure, while Expedia relies on it to consistently manage its vast and complex AWS environments, making it a powerful example of infrastructure as code in a single-cloud strategy.
This deep integration provides a reliable and consistent method for codifying and deploying AWS infrastructure, directly from the source.
Why and When to Use CloudFormation
CloudFormation is the ideal choice when your infrastructure lives entirely within the AWS ecosystem. Its key strength is its native integration, which simplifies IAM permissions and ensures immediate support for new AWS services. It uses the concept of "Stacks," which are manageable units of AWS resources. This makes it easy to create, update, or delete an entire collection of resources as a single unit. The service also features automatic rollback on error, which reverts your infrastructure to its last known stable state if a deployment fails, significantly reducing risk.
Actionable Tips for Implementation
- Use Change Sets for Previews: Before applying changes to a stack, always generate a change set. This acts like a "dry run," showing you exactly which resources CloudFormation will create, update, or delete, helping you prevent unintended and potentially costly modifications.
- Implementation Command (AWS CLI):
aws cloudformation create-change-set \ --stack-name my-production-stack \ --template-body file://updated-template.yaml \ --change-set-name my-change-set # After reviewing, execute the change set: aws cloudformation execute-change-set \ --change-set-name my-change-set \ --stack-name my-production-stack
- Implementation Command (AWS CLI):
- Leverage Nested Stacks: For complex architectures, break down your main template into smaller, reusable components called nested stacks. You can have a nested stack for your networking layer (VPC, subnets) and another for your application layer, which improves modularity and maintainability.
- Implementation Code (Root Stack):
Resources: NetworkingStack: Type: AWS::CloudFormation::Stack Properties: TemplateURL: https://s3.amazonaws.com/my-templates/networking.yaml Parameters: VpcCidr: 10.0.0.0/16
- Implementation Code (Root Stack):
- Parameterize Your Templates: Use the
Parameterssection to pass in runtime values like instance types or environment names. This makes your templates reusable across different environments (e.g., dev, staging, prod) without modifying the core template code. For more advanced implementations, explore how to get the most out of AWS CloudFormation services.- Implementation Code (Template Snippet):
Parameters: EnvironmentName: Type: String Description: The name of the environment (e.g., dev, prod). Default: dev Resources: MyS3Bucket: Type: AWS::S3::Bucket Properties: BucketName: !Sub "my-app-data-${EnvironmentName}"
- Implementation Code (Template Snippet):
3. Ansible
Ansible is an open-source automation platform that simplifies configuration management, application deployment, and infrastructure orchestration. It uses a human-readable language, YAML, to create "playbooks" that define automation jobs. Unlike many other tools that require agents on managed nodes, Ansible is agentless, typically communicating over standard SSH or WinRM protocols. This makes it incredibly lightweight and easy to start using.
While often categorized as one of the best configuration management tools on opsmoon.com, Ansible's powerful modules for cloud providers like AWS, Azure, and Google Cloud also make it a strong contender for infrastructure provisioning. Companies like BMW use Ansible Tower to manage and automate their complex infrastructure, while Hootsuite leverages it to streamline application deployments, demonstrating its dual strength in both provisioning and configuration, a key feature in many infrastructure as code examples.
Its procedural, step-by-step approach offers a different paradigm compared to declarative tools, giving engineers fine-grained control over the entire automation workflow.
Why and When to Use Ansible
Ansible shines when you need a single tool to handle both initial infrastructure provisioning and ongoing configuration management. Its agentless architecture and simple YAML syntax lower the barrier to entry, making it ideal for teams who want to automate quickly without a steep learning curve. It is particularly effective for orchestrating complex, multi-tier application deployments where the order of operations is critical.
Actionable Tips for Implementation
- Use Ansible Vault for Secrets: Securely manage sensitive data like API keys and passwords using Ansible's built-in encryption feature, Ansible Vault. This keeps your secrets out of plaintext version control.
- Implementation Commands:
# Create an encrypted variables file ansible-vault create secrets.yml # Edit an existing encrypted file ansible-vault edit secrets.yml # Run a playbook with the vault password ansible-playbook my_playbook.yml --ask-vault-pass
- Implementation Commands:
- Organize Playbooks with Roles: Structure your automation code into "roles," which are reusable collections of tasks, handlers, variables, and templates. This promotes modularity and makes your playbooks cleaner and easier to maintain.
- Example Role Structure:
roles/ ├── webserver/ │ ├── tasks/main.yml │ ├── handlers/main.yml │ ├── templates/httpd.conf.j2 │ └── vars/main.yml
- Example Role Structure:
- Leverage Dynamic Inventories: For cloud environments, use dynamic inventory scripts. These scripts query your cloud provider's API to automatically generate an up-to-date list of your hosts, eliminating the need for manual inventory management.
- Implementation Example (aws_ec2 plugin): Create a file
my-aws-inventory.ymlplugin: aws_ec2 regions: - us-east-1 filters: tag:Environment: productionThen run your playbook:
ansible-playbook -i my-aws-inventory.yml deploy.yml
- Implementation Example (aws_ec2 plugin): Create a file
4. Pulumi
Pulumi is a modern, open-source infrastructure as code platform that empowers developers to use familiar programming languages to manage cloud resources. Instead of learning a domain-specific language like HCL, teams can leverage Python, TypeScript, JavaScript, Go, or C# to define, deploy, and manage their infrastructure. This approach brings the full power of general-purpose languages, including loops, conditionals, functions, and classes, directly into the infrastructure provisioning process.
One of Pulumi's key differentiators is its ability to bridge the gap between application code and infrastructure code. By using the same language for both, it enables better collaboration, code reuse, and advanced automation patterns. For example, Snowflake uses Pulumi to manage its complex cloud environment with Python, while Mercedes-Benz leverages it for their cloud transformation initiatives. This makes it a compelling infrastructure as code example for organizations seeking to unify their development and operations workflows under a single programming model.
The ability to use real programming languages allows for more sophisticated logic and abstractions, enabling teams to build highly dynamic and reusable infrastructure components.
Why and When to Use Pulumi
Pulumi shines in environments where development teams are already proficient in one of its supported languages and want to avoid the context-switching of a separate DSL. It is ideal for building complex, application-aware infrastructure, where the infrastructure's configuration might depend on application logic. Using Pulumi, you can write unit and integration tests for your infrastructure code just as you would for application code, significantly improving reliability and catching errors before deployment. Its state management is similar to Terraform's, providing a reliable source of truth and safe, predictable updates.
Actionable Tips for Implementation
- Organize with Components: Use Pulumi Components to create high-level, reusable abstractions. A component can encapsulate a set of related resources, like a complete VPC with subnets and security groups, presenting a simple interface to consumers and hiding complexity.
- Implementation Code (TypeScript):
import * as pulumi from "@pulumi/pulumi"; import * as aws from "@pulumi/aws"; class VpcComponent extends pulumi.ComponentResource { public readonly vpcId: pulumi.Output<string>; public readonly publicSubnetIds: pulumi.Output<string[]>; constructor(name: string, args: {}, opts?: pulumi.ComponentResourceOptions) { super("custom:resource:VpcComponent", name, args, opts); // ... logic to create VPC, subnets, etc. // this.vpcId = vpc.id; } }
- Implementation Code (TypeScript):
- Implement Unit Tests: Take full advantage of using a general-purpose language by writing unit tests for your infrastructure logic. Use standard testing frameworks like Pytest for Python or Jest for TypeScript to validate resource configurations and custom logic before running
pulumi up.- Implementation Example (Jest for TypeScript):
// my_stack.test.ts import * as pulumi from '@pulumi/pulumi'; import 'mocha'; // Mock Pulumi's runtime pulumi.runtime.setMocks({ // ... mock provider calls }); describe('MyStack', () => { // ... your tests here });
- Implementation Example (Jest for TypeScript):
- Leverage Stack References: Use Stack References to share outputs between different stacks. This is crucial for managing dependencies between environments, such as allowing a production application stack to securely access the ARN of a database created in a separate production data stack.
- Implementation Code (TypeScript):
// In the app stack const dataStack = new pulumi.StackReference("my-org/data-stack/prod"); const dbArn = dataStack.getOutput("databaseArn");
- Implementation Code (TypeScript):
5. Azure Resource Manager (ARM) Templates
Azure Resource Manager (ARM) Templates are Microsoft's native infrastructure as code (IaC) solution for its cloud platform. These templates use a JSON-based declarative syntax to define and deploy Azure resources, from virtual machines to complex networking configurations. Instead of manual portal configurations, you define all your resources and their properties in a single JSON file, which ARM then uses to create, update, or delete resources in a consistent and repeatable manner.
A key strength of ARM is its deep integration with the Azure ecosystem. It provides robust dependency management, parameter support, and seamless integration with Azure services like Azure Policy, Azure Blueprints, and Azure DevOps. This makes it a go-to for organizations heavily invested in the Microsoft stack. For instance, enterprises like H&R Block and GEICO leverage ARM templates to automate and standardize the deployment of their core Azure environments, ensuring compliance and operational consistency in their infrastructure as code examples.
This native integration allows for precise control over Azure resources and their lifecycle, making it an excellent choice for Azure-centric cloud infrastructure management services.
Why and When to Use ARM Templates
ARM templates are the ideal choice when your infrastructure lives exclusively within the Azure cloud. They excel at orchestrating complex deployments with intricate dependencies between Azure resources, as the platform natively understands these relationships. ARM's validation engine can check your template for syntax errors and potential deployment issues before you even start, reducing the risk of failed deployments.
The use of parameter files separates configuration from logic, allowing you to reuse the same template for different environments (e.g., dev, staging, prod) simply by swapping the parameters. This is a powerful feature for teams managing multiple application stages.
Actionable Tips for Implementation
- Use Linked and Nested Templates: For complex deployments, break your main ARM template into smaller, reusable linked templates. This modular approach simplifies management and makes your infrastructure definitions easier to understand and maintain.
- Implementation Code (Main Template):
"resources": [ { "type": "Microsoft.Resources/deployments", "apiVersion": "2020-06-01", "name": "linkedStorageTemplate", "properties": { "mode": "Incremental", "templateLink": { "uri": "[uri(deployment().properties.templateLink.uri, 'linkedTemplates/storageAccount.json')]", "contentVersion": "1.0.0.0" }, "parameters": { ... } } } ]
- Implementation Code (Main Template):
- Leverage Template Functions: Use ARM's built-in functions to create dynamic values for resource names, locations, or other properties. This avoids hardcoding and makes your templates more flexible and powerful.
- Implementation Code:
"resources": [ { "type": "Microsoft.Storage/storageAccounts", "name": "[concat('storage', uniqueString(resourceGroup().id))]", "location": "[resourceGroup().location]", ... } ]
- Implementation Code:
- Validate Before Deployment: Always use the Azure CLI or PowerShell to validate your template before deploying it. This pre-deployment check catches errors early and can save significant time and prevent misconfigurations in your environment.
- Implementation Command (Azure CLI):
az deployment group validate \ --resource-group myResourceGroup \ --template-file ./template.json \ --parameters @./parameters.json
- Implementation Command (Azure CLI):
6. Google Cloud Deployment Manager
Google Cloud Deployment Manager is Google's native infrastructure as code (IaC) service, allowing teams to define, deploy, and manage Google Cloud Platform (GCP) resources declaratively. It uses simple YAML for configuration or, for more complex scenarios, can leverage the full power of Python or Jinja2 templates. This approach allows you to specify your desired infrastructure state, and Deployment Manager takes care of creating and configuring the resources in the correct order.
A key advantage of Deployment Manager is its deep integration with the GCP ecosystem. As a first-party tool, it often receives day-one support for new GCP services and features. This native alignment makes it a straightforward choice for teams operating exclusively within the Google Cloud. For instance, PayPal leverages Deployment Manager to provision consistent and secure GCP environments for its financial services, while Philips Healthcare uses it to manage cloud resources for its health-tech platforms, demonstrating its value in regulated and large-scale infrastructure as code examples.
This tight integration ensures that all API-level controls and resource options are directly available, providing granular control over your GCP infrastructure.
Why and When to Use Google Cloud Deployment Manager
Deployment Manager is an ideal choice when your infrastructure is entirely hosted on Google Cloud and you want a simple, native solution without introducing third-party tools. Its declarative model, combined with features like previews and dependency management, helps prevent configuration drift and ensures deployments are predictable. The ability to use Python templates also opens the door to programmatic and dynamic infrastructure generation, a powerful feature for complex, logic-driven deployments.
If your organization is deeply invested in GCP and prefers a native toolset that aligns perfectly with Google's services and IAM policies, Deployment Manager is a highly effective option.
Actionable Tips for Implementation
- Start Simple with YAML: Begin with basic YAML files to define your resources. This is the easiest entry point for learning Deployment Manager and is sufficient for many common use cases like provisioning a VM instance or a Cloud Storage bucket.
- Implementation Code (YAML):
resources: - name: my-first-vm type: compute.v1.instance properties: zone: us-central1-a machineType: zones/us-central1-a/machineTypes/e2-medium # ... other properties
- Implementation Code (YAML):
- Embrace Python for Complexity: When your configurations require conditional logic, loops, or dynamic property generation, transition to Python templates. This allows you to create sophisticated, reusable, and maintainable infrastructure blueprints that YAML alone cannot support.
- Implementation Example (Python Template Logic):
# vm_template.py def GenerateConfig(context): resources = [] for i in range(context.properties['num_vms']): resources.append({ 'name': f"vm-instance-{i}", 'type': 'compute.v1.instance', # ... properties }) return {'resources': resources}
- Implementation Example (Python Template Logic):
- Organize and Reuse with Composite Types: Group related resources into reusable units called composite types. Think of these as modules or building blocks, such as a complete web server stack (instance, firewall rule, disk), which you can then deploy as a single entity, simplifying management and reducing boilerplate.
- Validate with Schemas: Implement schema files for your templates. Schemas define the rules and constraints for your template properties, ensuring that anyone using the template provides valid inputs and helping to catch errors before deployment begins.
7. CDK (AWS Cloud Development Kit)
The AWS Cloud Development Kit (CDK) is an open-source software development framework that empowers developers to define cloud infrastructure using familiar, high-level programming languages like TypeScript, Python, Java, and C#. Instead of writing YAML or JSON, you write imperative code that describes your resources. This code is then synthesized into a standard AWS CloudFormation template, effectively giving you the best of both worlds: the expressive power of a programming language and the reliability of AWS's native provisioning engine.
This approach transforms infrastructure management into a software development discipline, enabling practices like code completion, inheritance, and unit testing for your cloud resources. This is a significant evolution in infrastructure as code examples, where companies like Stripe and Liberty Mutual leverage the AWS CDK to accelerate the development of serverless applications and manage complex AWS environments with greater agility and confidence.
The ability to use logic, loops, and object-oriented principles allows teams to create powerful, reusable abstractions for their infrastructure, dramatically reducing boilerplate and enforcing best practices.
Why and When to Use CDK
The AWS CDK is the ideal choice for development teams heavily invested in the AWS ecosystem who prefer to manage infrastructure using the same tools and languages they use for application code. It excels when you need to build complex or highly dynamic infrastructure, as you can use programming logic to generate resource configurations. This is particularly powerful for creating scalable, multi-tenant SaaS architectures or automated environments for development and testing.
Use CDK when your team values high-level abstractions and wants to move faster. Instead of defining every granular detail of a VPC, for instance, you can use a high-level construct that encapsulates AWS best practices, provisioning an entire production-ready network with just a few lines of code.
Actionable Tips for Implementation
- Start with High-Level Constructs: Leverage the AWS Construct Library to its fullest. These pre-built, opinionated components (L2 and L3 constructs) encapsulate best practices and significantly reduce the amount of code you need to write for common patterns like a Fargate service or a Lambda function connected to an API Gateway.
- Implementation Code (TypeScript L2 Construct):
import * as ec2 from 'aws-cdk-lib/aws-ec2'; import * as ecs from 'aws-cdk-lib/aws-ecs'; import * as ecs_patterns from 'aws-cdk-lib/aws-ecs-patterns'; // High-level construct that creates a Fargate service, task definition, // container, and load balancer with a single object. new ecs_patterns.ApplicationLoadBalancedFargateService(this, 'MyFargateService', { taskImageOptions: { image: ecs.ContainerImage.fromRegistry('amazon/amazon-ecs-sample'), }, publicLoadBalancer: true, });
- Implementation Code (TypeScript L2 Construct):
- Write Unit Tests for Infrastructure: Since your infrastructure is now defined in code, treat it like any other application. Write unit tests to validate your constructs' properties and ensure that changes don't introduce regressions or security vulnerabilities. This is a key advantage of CDK over declarative-only tools.
- Use
cdk diffReligiously: Before deploying, always run thecdk diffcommand. This command compares your current stack definition against the deployed version and provides a detailed summary of all pending changes, including security-sensitive modifications. This serves as a final, critical sanity check.- Implementation Commands:
# Synthesize the CloudFormation template cdk synth # Preview changes before deployment cdk diff # Deploy the stack cdk deploy
- Implementation Commands:
7 Key Infrastructure as Code Tools Compared
| Tool | Implementation Complexity | Resource Requirements | Expected Outcomes | Ideal Use Cases | Key Advantages |
|---|---|---|---|---|---|
| Terraform by HashiCorp | Moderate to high (HCL syntax) | Requires state file storage | Multi-cloud infrastructure provisioning, drift detection | Multi-cloud, reusable modules | Cloud-agnostic, strong state management, large ecosystem |
| AWS CloudFormation | Moderate (JSON/YAML templates) | AWS-native, no extra cost | AWS resource provisioning with rollback and dependency management | AWS-only cloud infrastructure | Deep AWS integration, automatic rollback, native service |
| Ansible | Low to moderate (YAML playbooks) | Agentless orchestration | System config, app deployment, hybrid infrastructure management | Configuration management, hybrid clouds | Agentless, easy YAML syntax, strong config management |
| Pulumi | High (general-purpose languages) | Supports multi-language IDEs | Programmable infrastructure with testing and abstraction | Developers using real languages | Uses real programming languages, testing, code reuse |
| Azure Resource Manager (ARM) | Moderate (complex JSON syntax) | Azure-native, no extra cost | Azure resources provisioning with parameterization and validation | Azure cloud infrastructure | Deep Azure integration, parameter support, rollback |
| Google Cloud Deployment Manager | Moderate (YAML/Python templates) | GCP-native, no extra cost | GCP resource deployment with flexible templating | GCP cloud infrastructure | Flexible template languages, schema validation |
| AWS Cloud Development Kit (CDK) | High (programming languages) | AWS-native, compiles to CloudFormation | AWS infrastructure as code with high-level abstractions and testing | Developers building AWS infra | Familiar languages, strong IDE support, reusable constructs |
Final Thoughts
Our deep dive into these real-world infrastructure as code examples has illuminated a fundamental truth: IaC is no longer a niche practice but the bedrock of modern, scalable, and resilient software delivery. Moving beyond theoretical discussions, we've analyzed tangible code from Terraform, CloudFormation, Ansible, Pulumi, and others to uncover the strategic thinking that separates a simple script from a robust, production-grade deployment pipeline. The examples showcased aren't just templates to be copied; they are blueprints for a new operational mindset.
The core lesson is that the choice of tool is often secondary to the principles you apply. Whether you prefer Terraform's declarative HCL, Pulumi's imperative code, or Ansible's procedural playbooks, the most successful implementations share common threads: modularity, reusability, and idempotency. Breaking down complex systems into smaller, manageable modules, as seen in our Terraform and Pulumi examples, is critical for maintainability and team collaboration.
Key Takeaways and Strategic Next Steps
To translate these insights into action, your focus should shift from "what tool to use" to "how to build a sustainable IaC practice." Based on our analysis, here are the most critical, actionable takeaways to implement immediately:
- Embrace a Modular Architecture: Start every new project by thinking in modules. Before writing a single line of code, ask yourself: "How can I break this system into reusable components?" This applies to a Terraform module for a VPC, an Ansible role for a web server, or a Pulumi component for a serverless application. This approach reduces code duplication and speeds up future deployments.
- Implement Strict State Management: As demonstrated with Terraform and CloudFormation, managing your state file is non-negotiable. Immediately implement remote state backends (like an S3 bucket or Azure Blob Storage) with locking mechanisms. This is the single most important step to prevent configuration drift and enable safe collaboration.
- Integrate IaC into CI/CD Early: Do not treat Infrastructure as Code as a separate, manual task. Your next step should be to integrate tools like
terraform planorpulumi previewdirectly into your pull request pipeline. This provides automated validation and a clear audit trail, making infrastructure changes as transparent and reliable as application code changes. - Prioritize Security with Policy as Code: Advance your practice by integrating security and compliance checks directly into your IaC workflow. Tools like Open Policy Agent (OPA) or Sentinel can enforce rules, such as preventing the creation of public S3 buckets or ensuring all databases are encrypted, before any infrastructure is ever provisioned.
Mastering these infrastructure as code examples is about more than just automating server deployment. It's about codifying your operational knowledge, enabling self-service for development teams, and building a foundation for elite-level DevOps performance. As you consider integrating Infrastructure as Code into your strategy to master DevOps, it's also insightful to explore broader industry discussions, such as those that propose completely different paradigms for managing operations. Some thought leaders are even exploring alternative approaches to traditional DevOps, pushing the boundaries of what's possible in operational efficiency.
Ultimately, the journey through these IaC patterns equips you to build not just products, but platforms for innovation. By transforming your infrastructure into a version-controlled, testable, and automated asset, you unlock unprecedented speed and reliability, allowing your organization to focus on what truly matters: delivering value to your customers.
Ready to implement these advanced IaC strategies but need expert guidance to ensure it's done right? OpsMoon offers on-demand, elite DevOps and SRE expertise to help you build, scale, and manage your cloud infrastructure with precision. Let our freelance platform engineers help you turn these OpsMoon examples into a production-ready reality.
