7 Key Infrastructure as Code Benefits for 2025
Discover the top infrastructure as code benefits, from cost savings to faster deployments. Get actionable tips and technical examples to transform your DevOps.
In modern software delivery, speed, reliability, and security are non-negotiable. Manually provisioning and managing infrastructure via cloud consoles or bespoke scripts is no longer a viable option; it's slow, error-prone, and impossible to scale effectively. This is where Infrastructure as Code (IaC) fundamentally changes the game. By defining and managing infrastructure—from networks and VMs to Kubernetes clusters and IAM policies—through machine-readable definition files, IaC applies proven software engineering practices like version control, testing, and modularity to your cloud or on-premise environments. The result isn't just automation, it's a strategic shift that unlocks unprecedented efficiency and control.
This article dives deep into the most critical infrastructure as code benefits, providing technical examples, actionable code snippets, and real-world scenarios to help you move from theory to implementation. We'll explore how declarative tools like Terraform and CloudFormation or procedural tools like Ansible and Pulumi don't just build servers, but build a more resilient, cost-effective, and collaborative engineering culture. For a deeper dive into the tools that enable this level of control and automation in the Azure environment, exploring guides like the one on Mastering the Azure PowerShell Module can provide valuable insights. Prepare to see how codifying your infrastructure is the cornerstone of high-performing DevOps.
1. Absolute Version Control and Auditable Change Tracking with GitOps
One of the most profound infrastructure as code benefits is the ability to manage your cloud and on-premise resources with the same rigor software developers use for application code. By placing your infrastructure definitions (e.g., .tf files for Terraform, manifest.yaml for Kubernetes) in a version control system like Git, you transform infrastructure management from an opaque, manual task into a transparent, programmatic, and auditable process.
Every change, whether it's adjusting a load balancer's health_check timeout, modifying a 0.0.0.0/0 ingress rule on a security group, or scaling a Kubernetes Deployment replica count, is committed to your repository. This creates a complete, immutable history of your infrastructure's evolution. Each git commit is timestamped, attributed to a specific author, and includes a message explaining the "why" behind the change, providing unparalleled visibility for debugging and compliance audits.
How GitOps Revolutionizes Infrastructure Management
GitOps takes this concept a step further by establishing Git as the single source of truth for your infrastructure's desired state. Instead of an engineer running terraform apply from their local machine, a GitOps operator (like Argo CD or Flux) continuously monitors a specific branch in your Git repository. When it detects a drift between the state defined in Git and the actual state of your live infrastructure, it automatically triggers a reconciliation loop to align the live environment with the repository's definition.
This workflow enforces a strict, review-based process for all infrastructure modifications.
- Proposing a Change: An engineer creates a new branch (
git checkout -b feature/add-redis-cache) and submits a pull request (PR) with the proposed infrastructure change, such as adding a newaws_elasticache_clusterresource in a Terraform file. - Automated Validation: CI pipelines automatically run against the PR, performing static analysis (
terraform validate), security scans with tools liketfsecor Checkov, and policy checks using Open Policy Agent (OPA) to ensure the change complies with organizational standards (e.g., mandatory tagging, no public S3 buckets). - Peer Review: Colleagues review the PR's
diff, scrutinizing theterraform planoutput posted as a comment by the CI system. They discuss potential impacts and suggest improvements directly within the context of the code. - Approval and Merge: Once approved, the PR is merged into the main branch (
mainorproduction). This merge event is the trigger. The GitOps operator detects the new commit hash, pulls the updated code, and automatically executes theterraform applycommand to enact the change in the target environment.
This systematic approach provides a clear audit trail directly within Git, making it easy to answer critical questions for compliance and debugging: Who changed what (git blame), when did they change it (git log), and why (git show <commit_hash>)? If a deployment introduces a high-latency issue, reverting it is as simple as executing git revert <commit_hash>, which triggers the GitOps operator to roll back the infrastructure to its previous known-good state.
2. Consistency and Standardization Across Environments
Another of the core infrastructure as code benefits is the ability to eradicate configuration drift and ensure uniformity across all your environments. By defining infrastructure using code, you create a single, authoritative blueprint that can be deployed repeatedly, guaranteeing that your development, staging, and production environments are functionally identical. This eliminates the notorious "it works on my machine" problem, which often stems from subtle, undocumented differences like a missing IAM permission or a different firewall rule between environments.
This approach codifies best practices into reusable, version-controlled artifacts like Terraform modules or Helm charts. For instance, companies like Airbnb leverage standardized Terraform modules to provision consistent infrastructure for over 200 microservices. This means every new service gets the same networking (aws_vpc, aws_subnet), security (aws_security_group), and access (aws_iam_role) configuration by default, dramatically reducing human error and security vulnerabilities.
How to Enforce Standardization with IaC
Achieving consistency isn't just about using the same script; it's about building a system around reusable and validated patterns. By treating your infrastructure definitions as a product, you can enforce standards programmatically and scale best practices across the entire organization.
This workflow turns infrastructure provisioning into a predictable and reliable factory-like process.
- Create Reusable Modules: Develop a central library of versioned, reusable modules for common infrastructure patterns. For example, a
vpcmodule in Terraform would abstract away the complexity of creating a VPC, subnets, route tables, and internet gateways. Consumers of the module only need to provide high-level inputs likecidr_block. - Use Parameterized Configurations: Abstract environment-specific values (like instance sizes, replica counts, or DNS names) into separate variable files. A common pattern in Terraform is to use
dev.tfvars,stg.tfvars, andprod.tfvarsfiles. The core IaC code remains identical, and the CI/CD pipeline applies the correct variable file for the target environment:terraform apply -var-file="prod.tfvars". - Implement Automated Template Testing: Integrate automated tests into your CI/CD pipeline. For IaC, this involves using tools like Terratest (for Go), which can spin up real infrastructure from your code in a temporary account, run assertions against it (e.g., check if a web server returns a
200 OK), and then automatically tear it down. This proves the module works as expected before publishing a new version. - Enforce Policy as Code: Use tools like Open Policy Agent (OPA) or Sentinel to codify and automatically enforce organizational standards. You can write a policy that states, "All
aws_s3_bucketresources must haveversioning_enabled = trueand must not have a public read ACL." This policy is checked during theterraform planstage in CI, failing the build if a violation is detected.
This systematic approach ensures that every piece of infrastructure, from a single S3 bucket to a multi-region Kubernetes cluster, is provisioned according to your organization's exact standards, improving reliability and security while accelerating project onboarding.
3. Faster Deployment and Provisioning
One of the most transformative infrastructure as code benefits is the dramatic acceleration of resource provisioning and environment deployment. By codifying infrastructure, you replace slow, click-driven manual setup processes with high-speed, parallelized automation. Teams can spin up entire complex ecosystems—including networking (VPCs, subnets), storage (S3 buckets, EBS volumes), compute (EC2 instances, ECS services), and databases (RDS instances)—in a matter of minutes instead of the days or weeks it traditionally takes.
This capability is a game-changer for business agility. For example, Shopify uses automated provisioning with IaC to flawlessly scale its massive infrastructure for peak traffic events like Black Friday. This speed isn't just about initial setup; it enables powerful workflows like creating ephemeral, production-identical environments for every pull request, allowing for comprehensive integration testing before code is ever merged.
How Automation Accelerates Time-to-Market
IaC tools like Terraform, AWS CloudFormation, and Pulumi parse your declarative configuration files, build a dependency graph of your resources, and then execute the necessary API calls to the cloud provider in the most efficient order possible (e.g., creating resources with no dependencies in parallel). This programmatic approach unlocks powerful, high-velocity workflows that were previously impossible.
This speed directly enables core DevOps practices like creating ephemeral environments for testing pull requests or conducting performance load tests against a production-identical stack, all without resource contention or manual effort.
- Design for Reusability: Create modular templates (e.g., Terraform modules, Helm charts) for common infrastructure patterns. For example, a
kubernetes-appmodule could encapsulate a KubernetesDeployment,Service,Ingress, andHorizontalPodAutoscaler, allowing developers to deploy their applications with just a few lines of code. - Implement Validation Gates: Embed automated health checks and validation steps directly into your deployment pipelines. After
terraform applycompletes, run a script that usescurlto check an application's health endpoint orpsqlto verify a database connection. The pipeline only proceeds if these checks pass, preventing the promotion of a broken deployment. - Manage Dependencies: Leverage the built-in dependency resolution of IaC tools. Terraform automatically infers dependencies (e.g., an
aws_instancedepends on theaws_subnetit's in). You can also usedepends_onto explicitly define non-obvious relationships, ensuring resources are always provisioned and configured in the correct sequence. - Employ Progressive Deployment: For large-scale changes, use CI/CD pipelines to orchestrate canary or blue-green deployments. For example, a pipeline can use Terraform to provision a new "blue" environment, run automated tests against it, and then use a weighted DNS record or load balancer rule to gradually shift traffic from the old "green" environment, minimizing risk.
By treating infrastructure provisioning as a repeatable, automated engineering task, you can build and tear down environments on demand. This empowers developers, accelerates testing cycles, and ultimately delivers value to customers faster.
4. Cost Optimization and Resource Management
Beyond automation and version control, one of the most compelling infrastructure as code benefits is its direct impact on your bottom line. By defining resources programmatically, you gain granular control over allocation, enabling automated strategies that systematically eliminate waste and optimize cloud spend. This shifts cost management from a reactive, manual cleanup task to a proactive, integrated part of your development lifecycle.
Every resource, from a db.t3.micro RDS instance to a 10-node Kubernetes cluster using m5.2xlarge instances, is specified in code. This codification allows you to enforce cost-conscious policies directly within your IaC templates and CI/CD pipelines, preventing over-provisioning before it ever happens. For example, instead of developers manually selecting oversized instances, you can define a policy that flags any aws_instance PR with a non-approved instance type.
How IaC Enables Proactive Cloud Cost Control
IaC provides the foundation for building a cost-aware engineering culture by making expenditure visible and controllable within the development workflow itself. Instead of receiving a surprise bill at the end of the month, teams can estimate costs during the planning phase and implement automated guardrails.
The following infographic highlights key metrics that organizations often achieve by applying IaC to their financial governance.
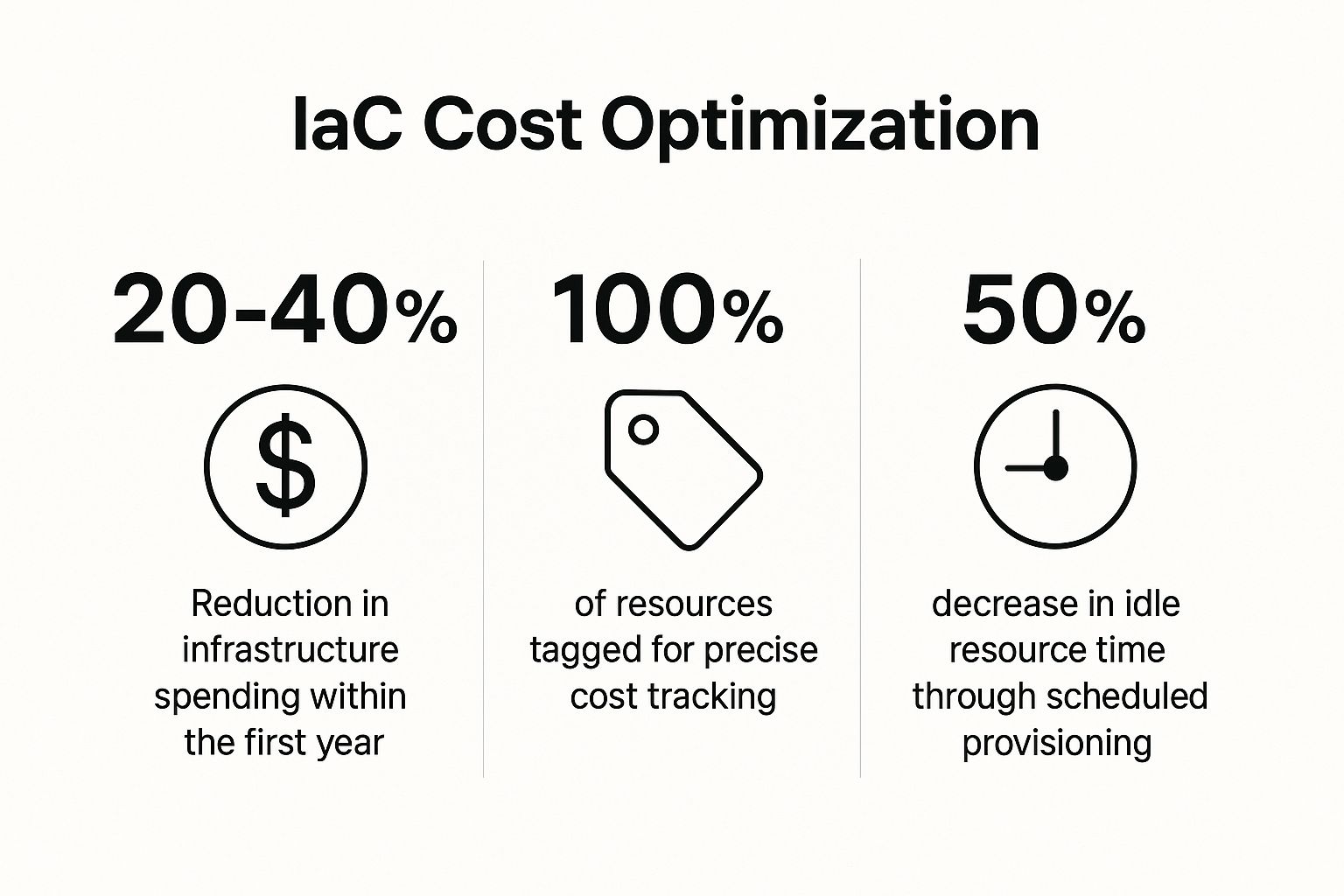
These figures demonstrate how programmatic control directly translates into significant savings, improved visibility, and greater resource efficiency. Here are some actionable strategies to achieve these results:
- Implement Automated Tagging: Enforce a mandatory tagging policy within your IaC modules using a
required_tagsvariable. Use tags liketeam,project, andcost-centerto allocate costs accurately, which is critical for showback and chargeback in tools like the AWS Cost and Usage Report. - Schedule Environment Shutdowns: Use CI/CD jobs (e.g., a scheduled GitHub Action) to run IaC scripts that automatically shut down non-production environments (development, staging) outside of business hours. This can be achieved with
terraform destroyfor ephemeral environments or by scaling down ASGs to zero. Coursera famously saves over $2M annually with this strategy. - Utilize Cost Estimation in CI: Integrate tools like Infracost or Terracost into your pull request pipeline. These tools parse the
terraform planand post a comment on the PR with an estimated monthly cost breakdown of the proposed changes (e.g., "+$500/month"), fostering financial accountability. - Define and Enforce Budgets as Code: Leverage cloud-native features like AWS Budgets or Azure Cost Management, defining them directly in Terraform. You can create an
aws_budgets_budgetresource that triggers an SNS notification or a Lambda function if spending exceeds a defined threshold. - Codify Auto-Scaling and Right-Sizing: Define auto-scaling policies (e.g.,
aws_appautoscaling_policy) in your IaC to match capacity with real-time demand based on metrics like CPU utilization or request count. Regularly use tools like AWS Compute Optimizer to identify underutilized resources and codify the "right-sized" instance types in your modules.
By embedding these practices into your code, you transform cost management from an afterthought into a core, automated component of your infrastructure. This approach aligns with modern FinOps principles and is a key part of effective cloud cost optimization strategies on opsmoon.com.
5. Enhanced Security and Compliance
One of the most critical infrastructure as code benefits is the ability to codify and automate security, transforming it from a manual, often-overlooked step into an integral part of the development lifecycle. By defining security policies, compliance controls, and configuration best practices directly within your IaC templates, you create a standardized, repeatable, and auditable security posture across all your environments.
This "security-as-code" approach ensures that every resource provisioned—from an aws_security_group to an aws_iam_policy—adheres to your organization's security standards from the moment of its creation. It eliminates configuration drift and manual errors that introduce vulnerabilities, such as an accidentally exposed database port. For instance, Goldman Sachs leverages Terraform with Sentinel policies to programmatically enforce that all S3 buckets have server-side encryption enabled and block public access.
How IaC Automates Compliance and Hardens Your Infrastructure
By treating security configurations as code, you can subject them to the same rigorous CI/CD processes used for application development. This means automated testing, peer reviews, and versioning are applied to your security rules, significantly reducing the risk of human error and creating a transparent, auditable trail for compliance frameworks like SOC 2, HIPAA, or PCI DSS. A practical example is how Dropbox maintains SOC 2 compliance using standardized infrastructure templates and automated auditing scripts that check live configurations against their code definitions in Git.
This systematic workflow embeds security directly into the deployment pipeline, a core principle of DevSecOps.
- Policy as Code: Use tools like HashiCorp Sentinel or Open Policy Agent (OPA) to define and enforce granular security policies. For example, you can write a Sentinel policy that prevents
terraform applyif anaws_security_group_rulecontainscidr_blocks = ["0.0.0.0/0"]for port 22 (SSH). - Automated Security Scanning: Integrate security scanners like
tfsec, Checkov, or Trivy directly into your CI pipeline. These tools scan your Terraform, CloudFormation, or Kubernetes files for hundreds of common misconfigurations (e.g., unencrypted EBS volumes, overly permissive IAM policies) and fail the build if any are found. - Immutable Infrastructure: IaC promotes the use of immutable infrastructure. Instead of SSHing into a server to apply a patch, you build a new, hardened Amazon Machine Image (AMI) using a tool like Packer, update the
amiID in youraws_instanceoraws_launch_templateresource, and roll out new instances to replace the old ones. This eliminates configuration drift and minimizes the attack surface. - Secrets Management: Integrate tools like HashiCorp Vault or AWS Secrets Manager with your IaC workflow. Your Terraform code references a secret (e.g.,
data "aws_secretsmanager_secret_version" "db_password") instead of hardcoding it. The IaC tool securely fetches the value at runtime and injects it into the resource configuration or application environment variables.
Adopting this proactive, code-driven security model allows your teams to move faster with confidence, knowing that a baseline of security and compliance is automatically enforced. It also simplifies audits, as your Git history provides a clear, verifiable record of every security-related change. For those looking to dive deeper, you can learn more about key principles and practices for embedding security into your CI/CD pipelines in our guide to DevOps security best practices.
6. Improved Disaster Recovery and Business Continuity
Another of the most critical infrastructure as code benefits is the ability to drastically shorten recovery times and enhance business continuity. By defining your entire infrastructure stack—from networking (VPC, Subnets, Route Tables) to compute (Auto Scaling Groups, Kubernetes clusters) to data services (RDS, ElastiCache)—in code, you create a portable and executable blueprint for your systems. In the event of a catastrophic failure, such as a regional cloud outage or a ransomware attack, this code becomes your fastest path to recovery.
Instead of relying on outdated runbooks and manual efforts to rebuild servers, you can simply execute your IaC templates in a different region. This approach transforms disaster recovery (DR) from a high-stress, unpredictable event into a repeatable, automated, and tested procedure, dramatically reducing your Recovery Time Objective (RTO) from days or weeks to mere hours or minutes.
How IaC Transforms Business Continuity Planning
IaC codifies your recovery plan, making it testable, versionable, and reliable. Companies like Square maintain exceptionally high uptime by managing their failover infrastructure with Terraform, allowing them to redirect traffic to a secondary region almost instantaneously by modifying a few DNS records, also managed as code.
This automated approach ensures your disaster recovery environment is an exact replica of your production setup, eliminating the configuration drift that often causes manual recovery efforts to fail.
- Automated Infrastructure Replication: Your IaC codebase (e.g., Terraform, CloudFormation) can be parameterized to deploy an identical infrastructure stack in a designated recovery region. A
providerblock in Terraform can be configured to targetus-west-2instead ofus-east-1, and the pipeline simply runsterraform applyagainst that new target. - Data Restoration Integration: The IaC scripts can include automated steps to restore data from backups. For instance, a Terraform
aws_db_instanceresource can be configured with thesnapshot_identifierargument pointing to the latest automated or cross-region replicated snapshot. The script can then provision a new database instance directly from that snapshot. - Regular, Automated Testing: Integrate DR drills directly into your CI/CD pipelines. A scheduled pipeline can periodically spin up the entire infrastructure in the recovery region, run a suite of integration and health-check tests to validate its functionality, and then tear it down using
terraform destroy. This practice, inspired by Netflix's chaos engineering, ensures your recovery plan actually works when you need it. - Rapid Failover Execution: When a disaster is declared, recovery is initiated by running a pre-approved IaC pipeline. This might involve promoting a read-replica database in the DR region to a primary instance, updating DNS records via an
aws_route53_recordresource, and scaling up compute resources, all orchestrated by the code.
By embedding disaster recovery into your engineering lifecycle, you move from a reactive "break-glass" model to a proactive, continuously validated state of readiness. This codification of your infrastructure is the cornerstone of a modern, resilient business continuity strategy.
7. Better Collaboration and Knowledge Sharing
Another one of the key infrastructure as code benefits is its power to break down knowledge silos and foster genuine cross-team collaboration. When infrastructure is defined as code and stored in a shared Git repository, it transforms from an opaque, specialized domain into a transparent, documented, and accessible asset for the entire engineering organization. This codification captures critical operational knowledge, preventing it from being locked away with individual "gurus" or specialized teams.
By treating infrastructure as a shared software project, you democratize expertise. Application developers can read the Terraform or Pulumi code to understand the environment their code will run in (e.g., "What environment variables are available? What are the firewall rules?"). Security teams can audit configurations programmatically, and new engineers can onboard faster by studying the codebase. This shared understanding reduces friction and handoffs, creating a more cohesive DevOps culture.
How IaC Becomes a Collaboration Hub
Adopting IaC fundamentally changes how teams interact with infrastructure, making collaboration the default standard. The process mirrors modern software development workflows, leveraging tools and practices that are already familiar to engineers, as famously championed by companies like Atlassian and GitHub.
This shift enables organizations to scale their expertise. For example, Spotify empowers its autonomous squads with self-service infrastructure capabilities by providing a "golden path" of well-documented IaC modules, allowing them to provision standard resources without lengthy handoffs.
- Implement Mandatory Code Reviews: Enforce a pull request (PR) process for all infrastructure changes. This practice ensures that every modification (e.g., a change to a load balancer rule) is reviewed by at least one other team member, who can scrutinize the code and the
terraform planoutput. This catches errors, shares architectural knowledge, and enforces best practices. - Create Comprehensive READMEs: Every infrastructure module or repository should have a detailed
README.mdfile. This document should follow a standard format, explaining the purpose of the infrastructure, its inputs and outputs, and providing copy-paste examples of how to use it. - Use Descriptive Naming and Comments: Write clean, self-documenting code. Use clear, consistent naming conventions for variables, resources, and modules (e.g.,
variable "database_password"instead ofvar_a). Add comments to explain complex logic or the "why" behind a specific configuration choice (e.g.,# This security group is intentionally open to allow for a public health check). - Maintain Architectural Decision Records (ADRs): For significant infrastructure decisions (e.g., "Why did we choose managed Kubernetes over rolling our own on EC2?"), create an ADR. This is a short markdown document in the repository that captures the context, decision, and consequences of an important architectural choice, providing invaluable historical context.
7 Key Benefits Comparison
| Aspect | Version Control and Change Tracking | Consistency and Standardization | Faster Deployment and Provisioning | Cost Optimization and Resource Management | Enhanced Security and Compliance | Improved Disaster Recovery and Business Continuity | Better Collaboration and Knowledge Sharing |
|---|---|---|---|---|---|---|---|
| Implementation Complexity | Moderate; requires disciplined commit and merge management | High; needs careful planning and refactoring | Moderate; upfront template creation plus dependency handling | Moderate; ongoing monitoring and expertise needed | High; requires security expertise and complex policy coding | High; planning multi-region and automated failover | Moderate; requires cultural shift and collaborative tooling |
| Resource Requirements | Standard source control systems (e.g., Git), infrastructure code | Template libraries, compliance tools, standardized modules | Automation tooling, CI/CD integration, deployment scripts | Cost management tools, tagging, scaling automation | Policy-as-code tools, security scanners, secrets management | Backup systems, multi-region infrastructure, automated failover | Shared repositories, code review tools, documentation effort |
| Expected Outcomes | Full audit trail, easy rollbacks, collaboration | Eliminates drift, consistent environments, reduced errors | Rapid deployments, faster scaling, shorter time-to-market | Reduced costs, right-sized resources, minimized waste | Consistent security policies, compliance, reduced risk | Fast recovery, high availability, reduced downtime | Shared knowledge, reduced silos, better onboarding |
| Ideal Use Cases | Large teams managing frequent infrastructure changes | Organizations needing uniformity across multiple environments | Teams requiring fast environment provisioning | Businesses aiming to optimize cloud spend | Regulated industries, security-sensitive environments | Critical systems needing fast disaster recovery | DevOps teams, multi-team infrastructure ownership |
| Key Advantages | Auditability, rollback, collaboration integration | Standardization, compliance, error reduction | Speed, scalability, integration with CI/CD pipelines | Cost savings, automation, detailed cost attribution | Security automation, policy enforcement, compliance auditing | Reduced RTO, automated failover, consistent recovery processes | Knowledge democratization, improved documentation, transparency |
From Code to Competitive Advantage: Your Next Steps with IaC
The journey through the core infrastructure as code benefits reveals a fundamental truth: modern, high-velocity engineering teams treat their infrastructure with the same discipline and rigor as their application code. This is no longer a niche practice but a strategic imperative for building resilient, scalable, and secure systems. Moving from manual configurations and siloed knowledge to a codebase that defines your entire operational environment is a powerful transformation.
As we've explored, the advantages are not abstract concepts; they are tangible, measurable improvements across your organization. You gain the ability to replicate complex environments with a single command, track every infrastructure change in a Git repository, and embed security policies directly into your deployment pipelines. This shift fundamentally redefines what's possible, turning slow, error-prone manual processes into fast, repeatable, and reliable automated workflows.
Synthesizing the Key Benefits
Let's distill the most critical takeaways from our discussion. The true power of IaC lies in the synergy between these benefits:
- Ultimate Traceability: By leveraging version control (Benefit #1), every change is auditable, reversible, and transparent. This pairs directly with enhanced security (Benefit #5), as you can pinpoint exactly who changed what, when, and why, satisfying even the strictest compliance requirements.
- Speed with Guardrails: Faster deployments (Benefit #3) are a direct result of codified consistency (Benefit #2). When every environment is a perfect, drift-free replica, you can promote changes from development to production with unparalleled confidence and speed.
- Financial and Operational Resilience: IaC enables proactive cost optimization (Benefit #4) by allowing you to define and enforce resource standards. This financial governance is the perfect complement to robust disaster recovery plans (Benefit #6), where you can rebuild your entire infrastructure from code in a new region, minimizing downtime and protecting revenue.
Ultimately, by codifying your infrastructure, you are also codifying your team's operational expertise. This improves collaboration and knowledge sharing (Benefit #7), breaking down information silos and turning tribal knowledge into a shared, version-controlled asset. This creates a durable competitive advantage, allowing you to innovate faster and operate more efficiently than competitors still wrestling with manual processes.
Your Actionable Roadmap to IaC Maturity
Embracing the full spectrum of infrastructure as code benefits is a journey, not a destination. To move forward, focus on these concrete next steps:
- Start Small, Prove Value: Select a non-critical service or a new project. Use a tool like Terraform or Pulumi to define its basic infrastructure (e.g., an S3 bucket for static hosting or a single EC2 instance with a security group). The goal is to build a small, successful proof-of-concept to gain buy-in and practical experience.
- Establish a "Source of Truth": Create a dedicated Git repository for your new IaC code. Enforce a pull request workflow for all changes, no matter how small. Protect your
mainbranch and require at least one approval before merging. This initial discipline is the foundation for everything that follows. - Integrate and Automate: Connect your IaC repository to a CI/CD pipeline (like GitLab CI, GitHub Actions, or Jenkins). Create two stages: a
planstage that runs on every PR, and anapplystage that runs automatically on merge tomain. This ensures that code is validated and deployed systematically, not from a developer's laptop.
Adopting IaC is more than an IT upgrade; it’s a strategic business decision. It is the technical foundation that allows you to out-maneuver competitors, deliver value to customers faster, and build a more resilient and secure business. The initial investment in learning, tooling, and process change pays dividends in speed, stability, and security for years to come.
Struggling to translate IaC theory into practice or need to accelerate your cloud-native journey? OpsMoon connects you with the top 0.7% of elite DevOps and platform engineers who specialize in architecting and implementing robust IaC solutions. Get expert help to build your cloud foundation right by visiting OpsMoon to start your risk-free work planning session.
