Top Container Security Scanning Tools for 2025
Discover the best container security scanning tools to safeguard your environment in 2025. Explore top solutions that ensure security and compliance.
The rapid adoption of containers has revolutionized software deployment, but it also introduces complex security challenges that demand more than a superficial check. A simple vulnerability scan is no longer sufficient. To fully understand the role of container security tools, it's helpful to differentiate between various security assessment methods, such as vulnerability scanning versus penetration testing. Modern DevOps and platform engineering teams require robust container security scanning tools that integrate seamlessly into the entire software development lifecycle (SDLC), from the developer's local machine all the way to production runtime.
This guide moves beyond marketing claims to provide a deeply technical and actionable breakdown of the top 12 tools available today. We will analyze their core scanning engines, CI/CD integration capabilities, vulnerability prioritization logic, and specific deployment use cases to help you choose, implement, and optimize the right solution for your environment. We'll explore everything from open-source powerhouses like Trivy and Grype to comprehensive enterprise platforms, focusing on practical implementation details and real-world trade-offs.
Our goal is to equip you, whether you're a CTO, an IT manager, or a platform engineer, with the precise information needed to make an informed decision. Each entry includes detailed analysis, screenshots for clarity, and direct links to the tools, helping you find the best platform for your technical needs and business scale. We will dissect how these tools address critical security concerns like detecting vulnerabilities in OS packages, application dependencies, infrastructure-as-code (IaC) configurations, and even secrets baked into container images. Let's get straight to the analysis.
1. Aqua Security (Aqua Platform + Trivy)
Aqua Security provides a powerful dual-offering approach to container security, making it one of the most versatile container security scanning tools available. Its strategy combines the widely adopted open-source scanner, Trivy, with its comprehensive commercial Cloud Native Application Protection Platform (CNAPP), the Aqua Platform. This allows teams to start with a robust, free scanner and scale into an enterprise-grade solution without switching ecosystems.
Trivy excels at fast, accurate scans directly within CI/CD pipelines, covering vulnerabilities in OS packages, language-specific dependencies, Infrastructure-as-Code (IaC) files, and secrets. The Aqua Platform builds on this foundation, adding centralized management, advanced risk scoring, and runtime protection. A key differentiator is its Dynamic Threat Analysis (DTA) feature, a sandboxing technology that executes container images to detect sophisticated malware, zero-day vulnerabilities, and other threats that static analysis might miss.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Trivy Open-Source Scanner | Integrating fast, free vulnerability scans into GitHub Actions, Jenkins, or local development workflows. |
| Dynamic Threat Analysis (DTA) | Securing production environments by analyzing untrusted or third-party images for hidden, behavior-based threats. |
| Comprehensive CNAPP | Enterprises requiring end-to-end security from code registry to Kubernetes runtime with policy enforcement. |
The platform integrates seamlessly with major registries, CI tools, and cloud providers, exporting results in formats like SARIF and CycloneDX for streamlined remediation workflows. Adhering to container security best practices is simplified with Aqua's extensive coverage. For teams evaluating their security posture, understanding these foundational principles is crucial; you can learn more about implementing container security best practices to complement your tooling choice. While the enterprise pricing for the Aqua Platform requires a sales consultation, the immense value provided by the free Trivy scanner makes Aqua an accessible entry point for any organization.
Website: https://www.aquasec.com/products/container-scanning/
2. Snyk Container
Snyk Container positions itself as a developer-first solution among container security scanning tools, focusing on integrating security seamlessly into existing workflows. Its core strength lies in providing actionable insights directly to developers, which speeds up remediation. By scanning not just the container image but also the underlying Dockerfile and Kubernetes configurations, Snyk offers contextual prioritization that helps teams focus on vulnerabilities that are truly exploitable in their specific application environment.
A key differentiator is its base image upgrade recommendation feature. Snyk intelligently identifies if a vulnerability can be fixed simply by upgrading to a newer, more secure base image and can even automate the process by creating a pull request. This direct, actionable approach significantly reduces the manual effort required to maintain a secure containerized environment. The platform's clear documentation and developer-friendly interface lower the barrier to adoption for engineering teams.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Developer-First Context | Teams looking to empower developers to fix vulnerabilities by providing clear, prioritized, and actionable guidance directly in their IDEs and PRs. |
| Base Image Upgrade Recommendations | Automatically identifying and fixing vulnerabilities by suggesting minimal-effort upgrades to parent images in Dockerfiles. |
| Kubernetes & Workload Scanning | Gaining visibility into running workloads to identify vulnerabilities that are actively exposed in a Kubernetes cluster. |
Snyk integrates smoothly with popular developer tools, including Docker Hub, major cloud container registries (ECR, GCR, ACR), and CI/CD systems like GitHub Actions and Jenkins. Its generous free tier, offering 100 container tests per month, makes it highly accessible for individual developers or small teams to start securing their containers immediately. For more advanced features like team-based policies and reporting, users will need to upgrade to paid Business or Enterprise plans.
Website: https://snyk.io/product/container-vulnerability-management/
3. Palo Alto Networks Prisma Cloud (Compute)
Palo Alto Networks Prisma Cloud offers one of the most comprehensive enterprise-grade container security scanning tools, extending far beyond basic vulnerability detection. Positioned as a full-lifecycle security platform, it excels in large, complex multi-cloud and hybrid environments where granular control and runtime defense are paramount. Its "Compute" module focuses specifically on securing hosts, containers, and serverless functions from development through production.
Prisma Cloud differentiates itself with its robust runtime protection and policy enforcement capabilities. It integrates directly into the CI/CD pipeline to scan images in registries like Docker Hub, Artifactory, and Quay, allowing teams to block vulnerable builds before deployment. A key feature is its admission controller for Kubernetes, which enforces "trusted image" policies, preventing un-scanned or non-compliant images from ever running in the cluster. This proactive gating mechanism is crucial for enterprises enforcing strict security and compliance standards across their cloud-native infrastructure.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Unified Registry & CI/CD Scanning | Organizations standardizing security checks across multiple development pipelines (Jenkins, GitHub Actions, CircleCI) and image registries. |
| Kubernetes Admission Controller | Implementing a zero-trust model in production clusters by automatically blocking deployments that violate security policies. |
| Advanced Runtime Defense | Protecting critical applications with deep process, file system, and network monitoring to detect and prevent anomalous behavior in real-time. |
The platform's strength lies in its ability to provide a single, unified view of risk across diverse environments. By correlating vulnerability data with runtime observations, it helps security teams prioritize the most critical threats. While its pricing is geared towards enterprises and requires a direct sales engagement, the platform's mature feature set provides a powerful, all-in-one solution for organizations seeking deep, integrated security from build to runtime. This makes it an ideal choice for large-scale deployments where consistency and control are non-negotiable.
Website: https://www.paloaltonetworks.com/prisma/cloud/container-security
4. Anchore (Enterprise) + Anchore Open Source (Syft/Grype)
Anchore differentiates itself with an SBOM-centric approach, positioning it as one of the top container security scanning tools for supply chain security. Similar to Aqua, it offers powerful open-source tools: Syft for generating Software Bill of Materials (SBOMs) and Grype for vulnerability scanning. This combination allows developers and DevOps teams to immediately integrate SBOM generation and vulnerability analysis into their CI/CD workflows, supporting formats like CycloneDX and SPDX.
The commercial Anchore Enterprise platform extends these capabilities for large-scale operations. Its core strength lies in storing and continuously analyzing SBOMs against updated vulnerability feeds. This means that even after an image is built and deployed, Anchore can alert teams to newly discovered vulnerabilities affecting its components without needing a full rescan. The platform provides centralized policy management, detailed reporting, and deep integrations with container registries and CI systems, making it ideal for enforcing compliance and security policies across an organization.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Syft & Grype Open Source | Developers needing to generate SBOMs and perform fast, accurate vulnerability scans directly in build pipelines. |
| SBOM-Centric Vulnerability Management | Organizations focused on federal compliance (e.g., EO 14028) and securing the software supply chain. |
| Centralized Policy & Reporting | Enterprises requiring auditable security and compliance records with granular policy enforcement across many teams. |
Anchore's focus on the SBOM as the central source of truth provides deep visibility into software dependencies, which is critical for modern application security. While Syft and Grype are free and highly effective for pipeline integration, leveraging the full potential of continuous monitoring and governance requires the paid enterprise platform. This dual-model provides a clear path for organizations to mature their container security posture from foundational scanning to comprehensive supply chain management.
Website: https://anchore.com/platform/secure/
5. Sysdig Secure
Sysdig Secure offers a runtime-centric approach to container security, making it a standout among container security scanning tools for teams looking to reduce alert fatigue. As a comprehensive Cloud Native Application Protection Platform (CNAPP), its core differentiator is the ability to correlate static scan results with live runtime insights. This allows it to prioritize vulnerabilities based on which packages are actually loaded and in use, effectively filtering out noise from packages that exist in an image but are never executed.
The platform provides both agentless and agent-based scanning options to fit different infrastructure needs, offering flexibility for cloud and on-premises deployments. It integrates directly with CI pipelines and popular registries like AWS ECR, automating vulnerability detection from development through to production. With its 'Scan Now' feature, teams can perform instant, ad-hoc scans on images, ensuring rapid feedback. Sysdig's focus on runtime context provides a practical advantage by helping engineers focus their remediation efforts on the threats that pose a genuine risk to their active applications.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Runtime-Aware Vulnerability Prioritization | DevOps teams in complex environments looking to reduce alert noise and focus on vulnerabilities with a clear attack path. |
| Agentless & Agent-Based Scanning | Organizations requiring flexible deployment models to secure both managed cloud services and self-hosted Kubernetes clusters. |
| CI & Registry Integrations (e.g., AWS ECR) | Automating security checks for every build and push, catching vulnerabilities before they are deployed to production environments. |
Sysdig Secure’s emphasis on exploitability helps teams move beyond simple CVE matching to a more risk-based security posture. While pricing is quote-based and requires a sales consultation, its unique ability to contextualize vulnerabilities makes it a powerful choice for mature teams aiming to enhance the efficiency of their security operations. It's also worth noting that users of legacy Sysdig components may need to plan for a migration, as the platform has evolved its architecture.
Website: https://sysdig.com/pricing-secure/
6. JFrog Xray (with Artifactory)
JFrog Xray positions itself as a universal software composition analysis (SCA) solution, making it a powerful choice among container security scanning tools, especially for teams already embedded in the JFrog ecosystem. Its primary strength lies in its deep, native integration with JFrog Artifactory. This connection allows Xray to perform recursive scans, analyzing every binary component and dependency within your container images against its extensive vulnerability intelligence database.
Unlike standalone scanners, Xray leverages the rich metadata stored in Artifactory to provide a comprehensive impact analysis graph. This unique feature shows you exactly which images and artifacts are affected by a newly discovered CVE, enabling rapid, targeted remediation. It also facilitates a proactive "shift-left" approach by allowing you to define security policies that can automatically block vulnerable builds from being promoted or deployed, directly enforcing security compliance within your CI/CD pipeline. The continuous scanning capability ensures that even artifacts already in storage are re-evaluated against new security advisories.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Native Artifactory Integration | Organizations using JFrog Artifactory that need to automatically scan every artifact and its dependencies. |
| Impact Analysis Graph | Quickly identifying the full blast radius of a new zero-day vulnerability across all stored container images. |
| Policy-Based Enforcement | Preventing builds with critical vulnerabilities or non-compliant licenses from ever reaching production environments. |
Xray's functionality extends beyond containers to support a wide range of package formats, offering a unified view of risk across your entire software supply chain. It provides a Docker Desktop extension for local scanning and a powerful CLI for easy integration into any CI/CD workflow. While the tight coupling with Artifactory is its greatest asset, it can also be a consideration for teams not already using the JFrog Platform. Pricing is available through various subscription tiers on major cloud marketplaces, though some advanced features are reserved for higher enterprise plans.
Website: https://jfrog.com/xray/
7. Docker Scout
Docker Scout provides deeply integrated image analysis, making it one of the most developer-friendly container security scanning tools for teams already invested in the Docker ecosystem. It embeds security insights directly into the tools developers use daily, including Docker Desktop, Docker CLI, and Docker Hub. This "shift-left" approach delivers immediate feedback on vulnerabilities and supply chain issues, allowing for rapid remediation before images are pushed to registries.
The platform automatically analyzes images, generates a Software Bill of Materials (SBOM), and correlates findings with a real-time vulnerability database. Docker Scout's key differentiator is its seamless integration, which removes the friction often associated with adopting a new security tool. By presenting actionable remediation advice directly in the command line or Docker Desktop UI, it empowers developers to fix issues on their local machines, significantly reducing the security team's workload and speeding up development cycles.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Local Image Analysis | Developers looking to scan and fix vulnerabilities in container images directly on their machine before committing code. |
| Policy Evaluation | Platform engineering teams enforcing organizational security and licensing standards across all development projects. |
| Docker Hub Integration | Teams needing continuous, automated security monitoring for images stored in Docker Hub repositories. |
Docker Scout is included with paid Docker subscriptions (Team and Business plans), making it a cost-effective choice for organizations already utilizing these tiers. It provides a simple setup and a unified user experience across the Docker product suite. However, users on Personal or Pro plans will find their access to Scout-enabled repositories limited, requiring an upgrade to unlock its full potential for organization-wide security management. This tight ecosystem focus makes it an exceptional tool for Docker-centric workflows but less of a standalone solution for heterogeneous environments.
Website: https://www.docker.com/products/docker-scout/
8. Tenable Cloud Security (Kubernetes and Container Image Scanning)
Tenable extends its industry-leading vulnerability management expertise into the cloud-native space with Tenable Cloud Security. Positioned as a key module within its unified exposure management platform, this solution offers a holistic approach by combining container image scanning with Kubernetes Security Posture Management (KSPM). This makes it one of the most compelling container security scanning tools for organizations already invested in the Tenable ecosystem for broader infrastructure security.
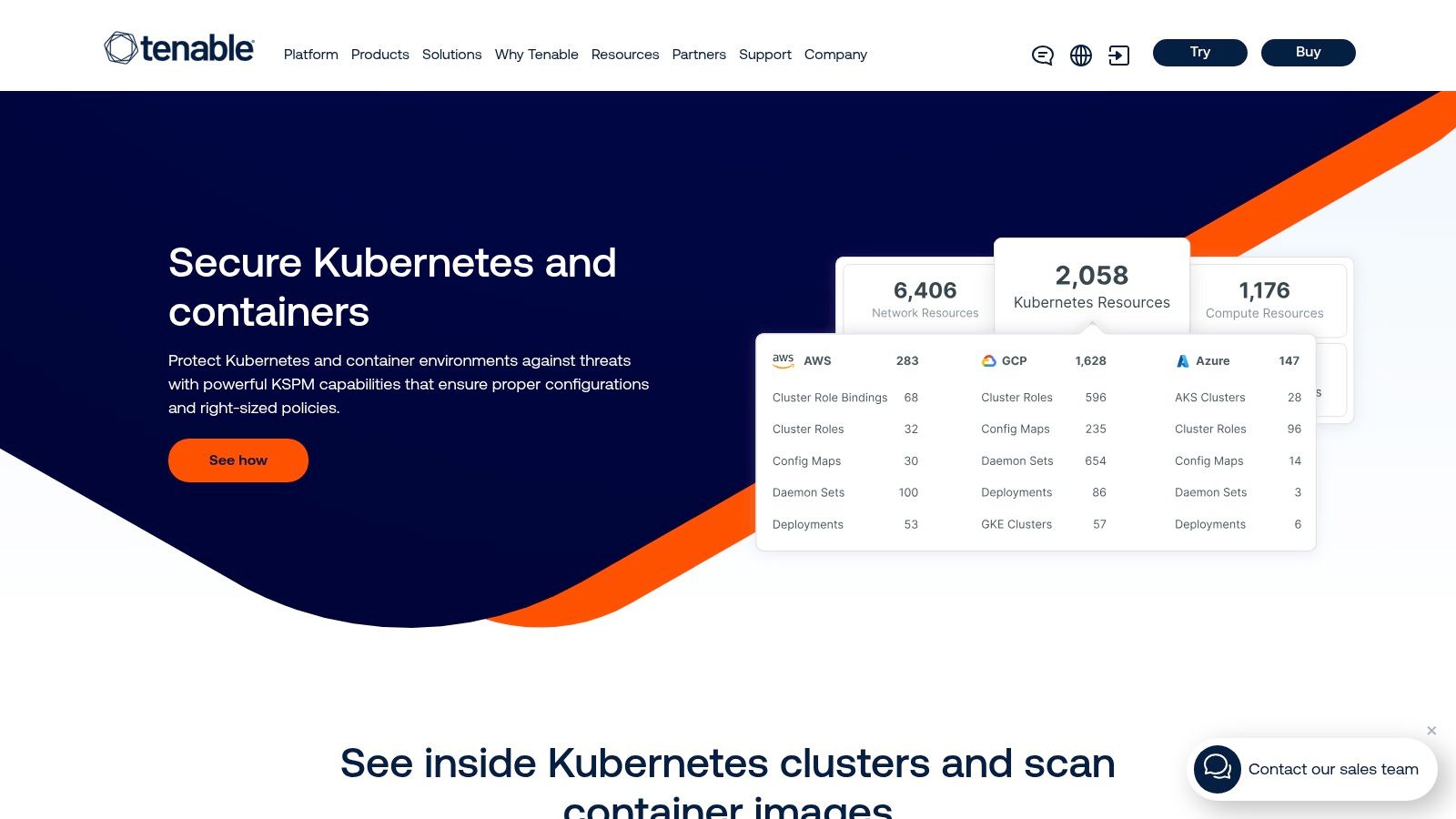
The platform’s strength lies in its ability to provide a single pane of glass for risk across diverse assets, from traditional servers and VMs to modern containerized workloads. Its scanner detects OS and application-level vulnerabilities, as well as malware, within container images before they are deployed. The KSPM capabilities complement this by continuously assessing the configuration of Kubernetes clusters, identifying misconfigurations, and validating security policies like least-privilege access, ensuring a secure runtime environment.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Unified Exposure Management | Organizations wanting to consolidate container, cloud, and on-prem vulnerability data into a single risk management dashboard. |
| Kubernetes Security Posture Management (KSPM) | Securing complex Kubernetes deployments by validating cluster configurations against security benchmarks and best practices. |
| Hybrid Environment Support | Enterprises managing a mix of on-premises and cloud-based Kubernetes services (like EKS, AKS, GKE) and needing consistent security coverage. |
Tenable's solution is designed for scale, integrating directly into CI/CD pipelines to shift security left and providing developers with actionable feedback early in the lifecycle. By correlating container vulnerabilities with other infrastructure risks, security teams can prioritize remediation efforts based on the actual business context and exposure. While pricing is often part of a larger platform bundle and can be opaque, the benefit of a unified security view makes it a powerful choice for existing Tenable customers aiming to secure their cloud-native applications.
Website: https://www.tenable.com/cloud-security/capabilities/kubernetes-container-image-scanning
9. Qualys Kubernetes and Container Security (KCS)
Qualys extends its well-established vulnerability management legacy into the cloud-native space with its Kubernetes and Container Security (KCS) module. As one of the more mature container security scanning tools, its strength lies in providing a unified view of risk that integrates container vulnerabilities with a broader asset management context. The platform offers continuous discovery of images and running containers, vulnerability scanning, and posture management for Kubernetes environments.
A key differentiator for Qualys KCS is its integration within the larger Qualys Cloud Platform. This allows security teams to correlate container-based threats with data from other IT assets, providing a holistic risk profile that many standalone tools lack. It enforces security policies through admission controllers and offers deep visibility into runtime behavior, helping teams maintain a strong security posture from development to production. The platform is designed to help teams effectively manage the entire lifecycle of their containerized applications, a critical component of a modern DevOps strategy.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Unified Asset & Risk View | Organizations that already use Qualys for VMDR and want to extend consistent vulnerability management to containers. |
| Admission Control Policies | Preventing the deployment of non-compliant or highly vulnerable images into a Kubernetes cluster at runtime. |
| Kubernetes Security Posture | Continuously assessing Kubernetes clusters against CIS benchmarks and other security standards for misconfigurations. |
Qualys integrates with CI/CD pipelines and major container registries, and its results can be pushed into ticketing systems like Jira to streamline remediation workflows. This makes it an effective solution for teams needing to manage complex, multi-faceted environments; for those navigating such complexities, you can explore more about specialized Kubernetes services to enhance your security and operational efficiency. While pricing is typically per-host and requires a sales consultation, Qualys offers a valuable free tier that provides visibility into your container environment, allowing teams to assess its capabilities before committing.
Website: https://www.qualys.com/apps/container-security/
10. Amazon Web Services: Amazon ECR Image Scanning + Amazon Inspector
For teams deeply embedded in the AWS ecosystem, leveraging native services for container security offers unparalleled integration and simplified billing. AWS provides a two-tiered approach to container security scanning directly within its Elastic Container Registry (ECR). This native functionality ensures that security analysis is a seamless part of the image management lifecycle, making it an essential component of an AWS-centric security strategy and one of the most convenient container security scanning tools for cloud-native teams.
The offering starts with a free basic scan, which uses the Clair open-source engine to detect OS package vulnerabilities on push. For more advanced needs, Amazon Inspector powers the enhanced scanning tier, providing continuous, automated rescans of images in ECR and those running on EKS or ECS. This enhanced capability adds language package vulnerability detection, generates a Software Bill of Materials (SBOM), and correlates findings with runtime context, helping prioritize the most critical threats.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Basic ECR Scanning | Teams needing a no-cost, automated vulnerability check for OS packages immediately upon pushing an image to ECR. |
| Inspector-Powered Enhanced Scanning | Organizations requiring continuous vulnerability management for both in-registry and running containers with detailed SBOMs. |
| Native Service Integration | AWS-native environments looking to consolidate security tooling and billing while leveraging runtime context from EKS and ECS. |
The primary advantage is the tight integration with AWS services, from IAM for permissions to EventBridge for triggering remediation workflows. While native AWS tools provide robust scanning, some organizations may seek additional expertise. Exploring options for an AWS managed service provider can help optimize these security configurations and integrate them into a broader cloud management strategy. Pricing is pay-as-you-go, with a free basic tier and a 15-day trial for Inspector, though costs for enhanced scanning can scale with image volume. You can learn more about how to integrate these AWS services for a complete security posture.
Website: https://aws.amazon.com/inspector/
11. Microsoft Defender for Containers (with ACR image scanning)
For organizations deeply embedded in the Azure ecosystem, Microsoft Defender for Containers offers a tightly integrated solution. It serves as a key component within the broader Defender for Cloud platform, providing native vulnerability scanning for images stored in Azure Container Registry (ACR) and runtime protection for Azure Kubernetes Service (AKS) clusters. This makes it an excellent choice among container security scanning tools for teams aiming to consolidate security management within a single cloud provider.
The platform's primary strength is its seamless integration. Vulnerability assessments are automatically triggered when images are pushed, pulled, or imported into ACR, feeding results directly into the Defender for Cloud security posture dashboard. This eliminates the need for third-party scanner configurations within the registry. Beyond static scanning, it extends protection to the runtime environment by monitoring for suspicious activities, enforcing security policies, and providing threat intelligence alerts for AKS clusters, creating a cohesive security fabric from registry to runtime.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Native ACR Image Scanning | Teams using Azure Container Registry who need automated, zero-configuration vulnerability scans on image push and pull events. |
| Kubernetes Runtime Protection | Securing AKS clusters by monitoring for threats, applying security policies, and generating alerts based on Microsoft's threat intelligence. |
| Centralized Security Posture | Organizations consolidating all cloud security operations within Microsoft Defender for Cloud for unified visibility and management. |
While the native integration is a significant advantage, some users report that its vulnerability detection can be less comprehensive than specialized, third-party tools. The quality of coverage may also vary based on specific image configurations. Pricing is handled on a pay-as-you-go model per vCore for agentless container posture management, with a free monthly allowance that makes it accessible for smaller workloads. This approach provides a frictionless path to container security for Azure-native development teams.
Website: https://azure.microsoft.com/pricing/details/defender-for-cloud/
12. Google Cloud Artifact Analysis (Artifact Registry container scanning)
For organizations deeply embedded in the Google Cloud ecosystem, Google Cloud's Artifact Analysis offers a highly integrated and native solution among container security scanning tools. It provides managed vulnerability scanning directly within Artifact Registry, Google's universal package manager. This tight integration simplifies the security workflow by automatically scanning container images upon push, eliminating the need for separate tool configuration for teams using GCP.
The service detects vulnerabilities in both OS packages and language-specific dependencies across a broad range of ecosystems. A key advantage is its continuous scanning capability, which re-scans recently pushed and pulled images as new vulnerability information becomes available from its data sources. This ensures that even idle images are kept up-to-date with the latest threat intelligence. Its clear, per-image pricing model and straightforward setup make it an accessible option for existing GCP users looking to secure their container lifecycle.
Key Features & Use Cases
| Feature | Best Use Case |
|---|---|
| Automatic On-Push Scanning | Teams using Google Cloud Build and Artifact Registry who want immediate vulnerability feedback without pipeline changes. |
| Continuous Analysis | Ensuring images stored for long periods in Artifact Registry are re-evaluated against newly discovered CVEs. |
| GCP Native Integration | Organizations looking for a frictionless, out-of-the-box scanning solution within their existing GCP environment. |
While automatic scanning is limited to images within Artifact Registry, on-demand scans can be triggered via the gcloud CLI, allowing for easy integration into custom CI/CD pipelines or local development checks. The scan results are directly accessible through the GCP console or API, providing clear severity ratings and remediation guidance. For teams committed to GCP, this tool offers a seamless and efficient way to embed security directly into their cloud-native development and deployment workflows without adding third-party complexity.
Website: https://cloud.google.com/artifact-analysis/
Container Security Scanning Tools Comparison
| Solution | Core Features | User Experience/Quality | Value Proposition | Target Audience | Price Points/Model |
|---|---|---|---|---|---|
| Aqua Security (Aqua Platform + Trivy) | End-to-end artifact scanning, Trivy OSS, DTA sandbox | Accurate, broad vuln coverage, ecosystem integrations | Strong free scanner, enterprise-grade controls | Enterprise & DevOps teams | Enterprise pricing via sales |
| Snyk Container | Continuous scanning, base image fixes, CI integrations | Developer-friendly, good docs, easy setup | Free tier for small teams, dev-centric | Small to mid-size dev teams | Free plan; paid tiers for features |
| Palo Alto Prisma Cloud (Compute) | Registry scanning, CI/CD gating, runtime defense | Mature runtime protections, multi-cloud support | Enterprise multi-cloud protection | Large enterprises | Enterprise pricing, sales contact |
| Anchore (Enterprise + OSS Syft/Grype) | SBOM-first, continuous vuln eval, CI integrations | Strong free OSS tools, deep SBOM focus | Supply chain security, attestation | Large orgs, supply chain security | Paid platform for enterprise features |
| Sysdig Secure | Registry/runtime scanning, priority on runtime use | Runtime-aware prioritization, AWS ECR integration | Reduced alert noise, strong AWS support | Enterprise & AWS users | Quote-based pricing |
| JFrog Xray (with Artifactory) | Recursive scanning, CVE rescanning, policy enforcement | Tight artifact mgmt integration, scalable | Enterprise readiness, DevOps platform | DevOps & enterprise orgs | Paid tiers, cloud marketplace plans |
| Docker Scout | Local image analysis, SBOM, Docker integration | Seamless with Docker tools, simple setup | Included with paid Docker plans | Docker users, dev teams | Included in Team/Business plans |
| Tenable Cloud Security | Container scanning, KSPM, cluster policy checks | Unified risk view, scales mixed envs | Broad risk exposure management | Cloud & hybrid security teams | Bundled pricing, sales contact |
| Qualys Kubernetes & Container Security | Continuous discovery, vuln scanning, KSPM | Mature, free view-only tier | Unified asset and risk mgmt | Enterprise security teams | Sales-based, cost scales by hosts |
| AWS: Amazon ECR Image Scanning + Inspector | Basic/enhanced ECR scanning, SBOM, CI integrations | Native AWS experience, pay-as-you-go | Free basic scan, enhanced optional | AWS customers | Pay-as-you-go, scaling with usage |
| Microsoft Defender for Containers | ACR image scanning, cluster policy, alerts | Native Azure integration, centralized billing | Integrated Azure Defender ecosystem | Azure users | Pay-as-you-go, monthly free scans |
| Google Cloud Artifact Analysis | Auto/on-demand scanning, broad package support | Simple GCP native setup, CI/CD friendly | Clear per-image pricing, native GCP | Google Cloud Platform users | Per-image pricing |
Orchestrating a Secure and Efficient DevOps Lifecycle
Selecting from the extensive list of container security scanning tools is a foundational step, but it is not the final destination. The true value of tools like Aqua Security, Snyk, or even cloud-native solutions like Amazon Inspector, is only unlocked when they are deeply woven into the fabric of your DevOps lifecycle. The goal is not just to find vulnerabilities, but to create a resilient, automated, and security-conscious software delivery pipeline that moves at the speed of your business.
This article has provided a detailed technical breakdown of leading scanners, from comprehensive enterprise platforms to powerful open-source command-line tools. We've explored their distinct scanning engines, their CI/CD integration capabilities, and their approaches to runtime security. The key takeaway is that there is no single "best" tool; the optimal choice is entirely dependent on your specific technical stack, team maturity, compliance requirements, and operational budget.
From Selection to Strategic Implementation
After evaluating the options, the next critical phase involves strategic implementation. This goes beyond simply running scans; it’s about making the output of these tools actionable and integrating them without introducing unnecessary friction for your development teams.
- Automate Everything: Your chosen tool must be integrated directly into your CI pipeline. Scans should trigger automatically on every commit or build, providing immediate feedback. A pull request that introduces a critical vulnerability should fail its checks, preventing insecure code from ever reaching the main branch.
- Define Your Policies: Don't treat all vulnerabilities equally. Establish clear, automated policies for what constitutes a build failure. For instance, you might block any new 'Critical' or 'High' severity vulnerabilities with known exploits, while logging 'Medium' or 'Low' findings for later review. Tools like Anchore and Prisma Cloud offer robust policy-as-code engines to manage this.
- Context is King: A raw list of CVEs is noise. The most effective container security scanning tools provide context. They help you understand if a vulnerable package is actually loaded into memory or reachable by an attacker. Use this context to prioritize remediation efforts on the risks that genuinely threaten your application.
- Integrate into the Developer Workflow: Security findings should not be siloed in a separate dashboard. Integrate alerts directly into the tools your developers already use, such as Slack, Jira, or Microsoft Teams. This ensures visibility and makes remediation a natural part of the development sprint, not a separate, burdensome task.
Making the Right Choice for Your Organization
Choosing the right tool requires a clear-eyed assessment of your needs. An early-stage startup might achieve significant security uplift by integrating the open-source Trivy or Grype into their GitHub Actions for free. In contrast, a large financial institution facing strict regulatory compliance will require an enterprise-grade solution like Sysdig Secure or Tenable Cloud Security, which offers comprehensive runtime protection, forensics, and detailed audit trails.
Consider your entire ecosystem. If your organization is heavily invested in JFrog Artifactory, then JFrog Xray is a natural fit, providing deep binary analysis within your existing registry. If you operate primarily within a single cloud provider, leveraging their native tools like Microsoft Defender for Containers or Google Cloud's Artifact Analysis can simplify procurement and integration significantly, although they may lack the advanced features of specialized third-party platforms. The ultimate decision hinges on balancing feature depth, integration simplicity, operational overhead, and cost.
Ultimately, adopting container security scanning is a cultural shift. It’s about empowering developers with the information they need to write secure code from the start and making security an intrinsic, shared responsibility across the entire engineering organization.
Navigating the complexities of selecting, implementing, and optimizing container security scanning tools requires specialized expertise. OpsMoon connects you with a global network of elite, pre-vetted remote DevOps and DevSecOps engineers who can help you build a secure, automated, and scalable infrastructure. Fortify your development lifecycle and accelerate your security posture by partnering with the experts at OpsMoon.
